EventTranscript.db contains many events of varying interests to DFIR examiners. Some of the most forensically relevant Event Names explored by Kroll were prefaced with Microsoft.Windows.ClipboardHistory.Service. Within Microsoft.Windows.ClipboardHistory.Service events, the following Event Names emerged:
- Microsoft.Windows.ClipboardHistory .Service.AddItemActivity
- Microsoft.Windows.ClipboardHistory .Service.ClipboardActivityMonitor _ConnectedToServerProxy
- Microsoft.Windows.ClipboardHistory .Service.ClipboardActivityMonitor _ConnectingToServerProxy
- Microsoft.Windows.ClipboardHistory .Service.ClipboardActivityMonitor _DisconnectedFromServerProxy
- Microsoft.Windows.ClipboardHistory .Service.ClipboardMonitor_Start
- Microsoft.Windows.ClipboardHistory .Service.ClipboardMonitor_Stop
- Microsoft.Windows.ClipboardHistory .Service.CopyActionDetected _Compliant
- Microsoft.Windows.ClipboardHistory .Service.LocalContentChangeListener _DoubleCopyOptInOpportunityInfo
- Microsoft.Windows.ClipboardHistory .Service.PasteActionDetected _Compliant
- Microsoft.Windows.ClipboardHistory .Service.ServiceInitializationActivity
- Microsoft.Windows.ClipboardHistory .Service.ServiceInitialization Phase2Activity
- Microsoft.Windows.ClipboardHistory .Service.ServiceStartActivity
- Microsoft.Windows.ClipboardHistory .Service.ServiceStopActivity
- Microsoft.Windows.ClipboardHistory .Service.SettingCensus
- Microsoft.Windows.ClipboardHistory .Service.UsageCensus
Research has not been conducted on most of these events yet, but Kroll identified the most forensically interesting as: Microsoft.Windows.ClipboardHistory. Service.CopyActionDetected_Compliant and Microsoft.Windows.ClipboardHistory. Service.PasteActionDetected_Compliant.
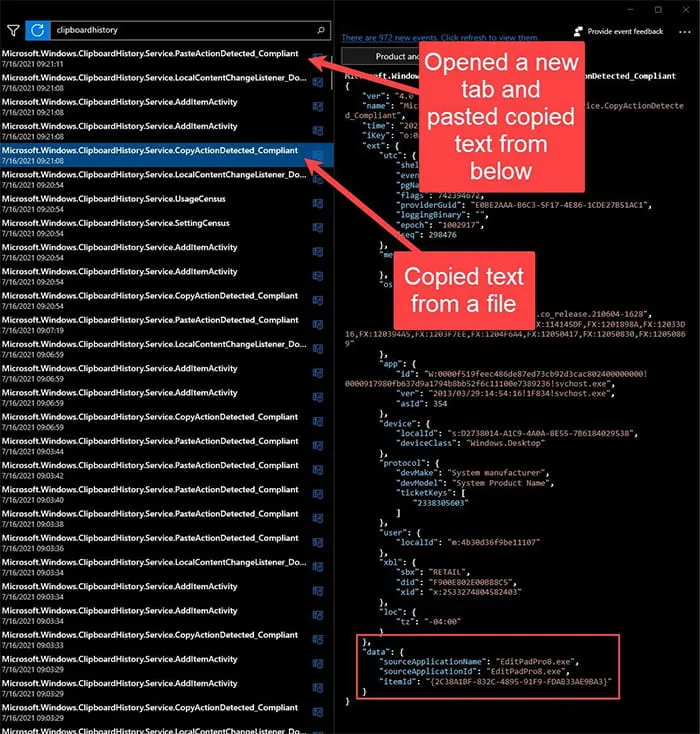
Kroll observed the CopyActionDetected_Compliant event whenever the action of copying content to the Windows Clipboard occurred. While this doesn’t show the content that was copied, unfortunately, it does provide the application from which the content was copied. In testing, Kroll observed the timestamp of this event to be consistent with when the action occurred in the testing environment and the sourceApplicationName value being consistently accurate.
Kroll tested a common, everyday scenario where an end user copies text from an application and pastes it elsewhere within the same application, like a text editor or an Office application. Kroll observed the following sequence of events:
- Microsoft.Windows.ClipboardHistory .Service.CopyActionDetected _Compliant
- Microsoft.Windows.ClipboardHistory .Service.AddItemActivity
- Microsoft.Windows.ClipboardHistory .Service.AddItemActivity
- Microsoft.Windows.ClipboardHistory .Service.LocalContentChangeListener _DoubleCopyOptInOpportunityInfo
- Microsoft.Windows.ClipboardHistory .Service.PasteActionDetected _Compliant
Below is what Kroll observed within Diagnostic Data Viewer when filtering on “clipboardhistory”.
Another scenario that Kroll tested was one where the user has six open worksheets in Excel, and the user copies content from one worksheet to the other five in rapid succession.
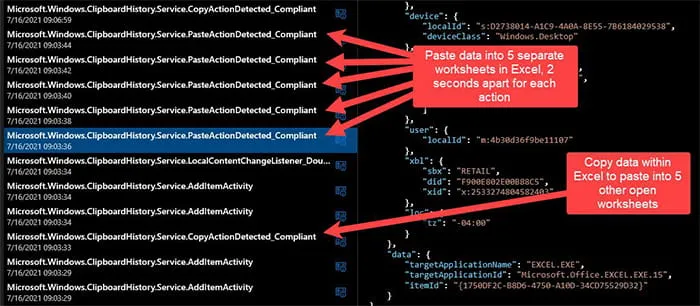
As is common with events stored within EventTranscript.db, you can pivot on the values stored within the JSON data to reveal other events related to that item. For instance, when you pivot on the itemId value, one will find the following related events:
- Microsoft.Windows.Shell .TaskFlow.DataEngine .HandleClipboardSignalInfo
- Microsoft.Windows .ClipboardHistory .Service.AddItemActivity
Kroll sees value in this artifact for providing potential insight into data exfiltration scenarios, where files/content from files were copied from a system and staged for exfiltration.

