EventTranscript.db provides both a potential boon and challenges for forensic investigations. Understanding the core components, database interaction and the artifact generation process is critical to maximizing the value generation of this sparsely documented functionality. This process is still underway; however, sufficient analysis has been accomplished to provide a generalized understanding.
Starting with a forensic image of a device, we identified the EventTranscript.db file located at C:\ProgramData\Microsoft\Diagnosis\EventTranscript\EventTranscript.db. This database clearly contained important information, but how was it being updated? First, we searched for processes with handles to the file. At the time, no results were found. This was most likely due to the testing environment being improperly configured, but we didn’t know what we were looking for at the time.
Investigating the directory structure and paths to EventTranscript.db led us to Microsoft documentation for the Windows functionality related to privacy, diagnostics and telemetry. No mention of the database file was found; however, we were armed with new information. Primarily, we had observed that there seemed to be a relationship between the database and the Windows telemetry and diagnostics subsystem.
Using this new information, we began searching for Windows services that could be associated with telemetry and diagnostics (Figure 1).
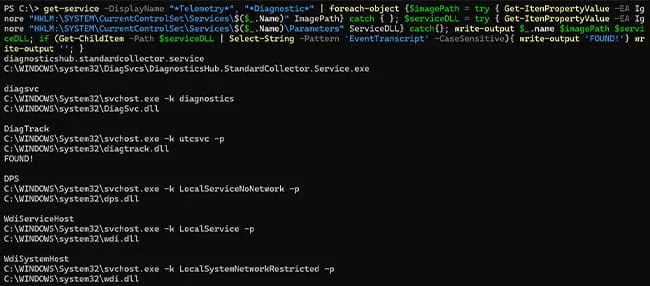
Figure 1: Service Searching
As shown in Figure 1, the DiagTrack service uses C:\windows\system32\diagtrack.dll and contains references to EventTranscript. Investigating this DLL with Ghidra, we find multiple references to EventTranscript.db, SQLite temporary files, service temporary files and Windows Registry.
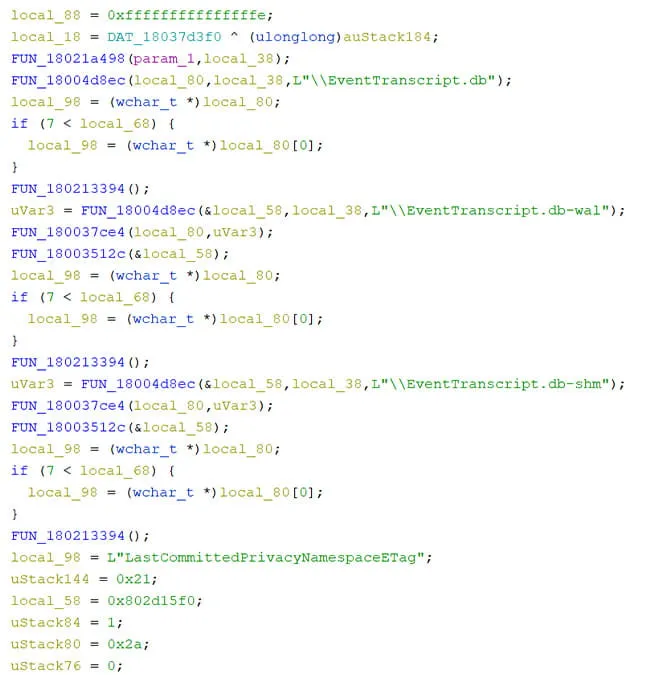
Figure 2: DiagTrack Database Interaction
Reviewing historical data for diagtrack.dll, we find that between version 1703 and 1709, diagtrack.dll consolidates diagnostic logging from events00.rbs, events01.rbs, events10.rbs and events11.rbs into EventTranscript.db. These changes correspond to the increased telemetry data collection between the aforementioned versions. Detailed analysis of the *.rbs files and associated telemetry data for the purposes of forensic analysis is outlined here. Using this newfound information, we can begin to decipher the Windows Registry components that dictate the behavior of this subsystem.


