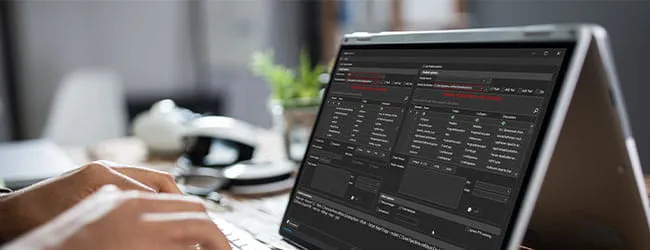
Security events and system health information related to the status of firewall and antivirus services are recorded in EventTranscript.db. Since threat actors typically modify these system settings, this data can be critical for establishing a coherent timeline and sequence of events that occurred during an incident. Furthermore, in the face of Event Log clearing, EventTranscript.db provides actionable items to assist in the investigation. To begin, disable various Windows security settings through the Windows Security GUI or command line (Figure 1).
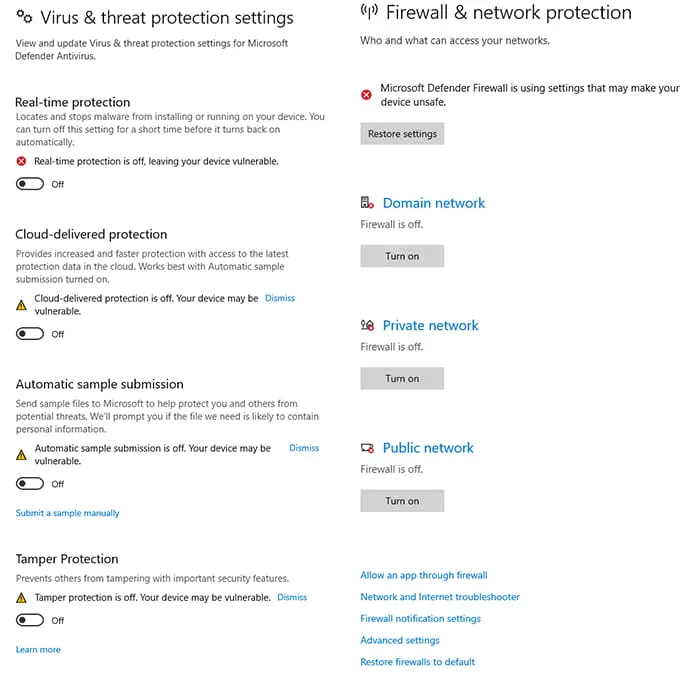
Figure 1: Disabled Windows Defender and Firewall
The changes to the services can be seen with the telemetry event: Microsoft.Windows.Defender.Shield.ShieldHeartbeat. Figure 2 shows the statuses of the different components when in a default configuration.
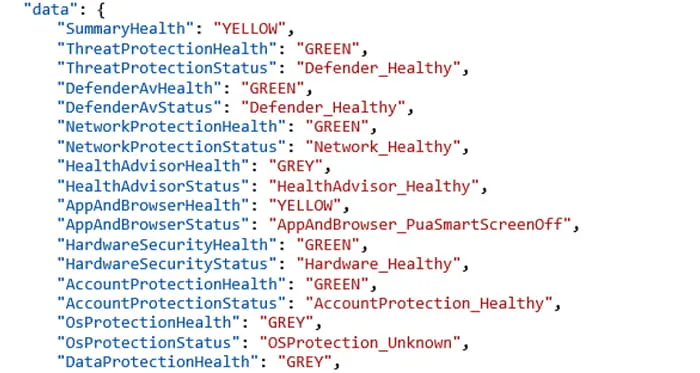
Figure 2: Security-Enabled Event Contents
With the settings disabled, Figure 3 shows how the values change. (Note: Firewall is not disabled in this screenshot.)
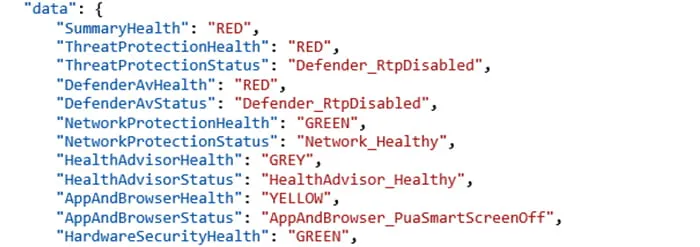
Figure 3: Security-Disabled Event Contents
As shown in Figure 3, when protections are disabled, the corresponding value changes in the event from GREEN to RED.
When Windows Defender is enabled, the telemetry event, Microsoft.Windows.Security.WSC.EnableDefender is fired (Figure 4). This event signals that Windows Defender is enabled with the enable key.
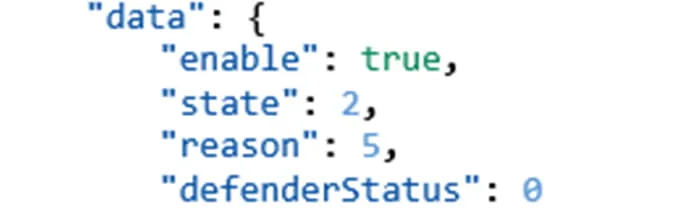
Figure 4: Defender-Enabled Event
Also, periodic service status events are triggered with the event name: Microsoft.Windows.Inventory.General.InventoryMiscellaneousServiceAdd (Figure 5). This event will show the execution status of the different services.
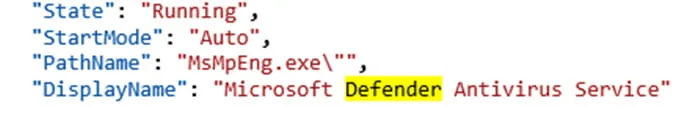
Figure 5: Service State Running
Disabling services will cause the event to change the State value (Figure 6).
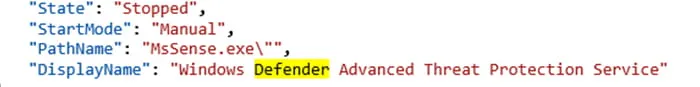
Figure 6: Service State Stopped
The type of installed antivirus software can be determined with the DisplayName and ProductState values found in the telemetry event: Microsoft.Windows.Inventory.General.InventoryMiscellaneousAntivirusInformationAdd (Figure 7).
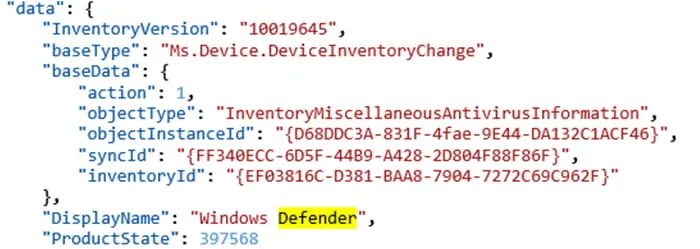
Figure 7: Antivirus Type
The ProductState value corresponds to the numerical identifier given for the installed antivirus software product and the product update status. This value corresponds to WSC_SECURITY_PRODUCT_STATE enum accessible via the IWscProduct interface.
Version information for the antivirus software signature database used by Windows Defender can be found in the telemetry event: Microsoft.Windows.Inventory.General.InventoryMiscellaneous.UUPInfoAdd (Figure 8).
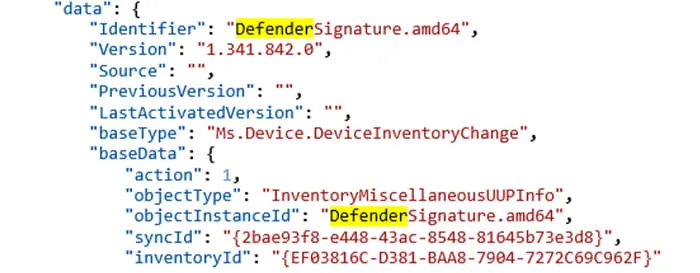
Figure 8: Defender Signature Version Event
In Figure 8, the Version key identifies the version of the antivirus software database as 1.341.842.0. This can be found with the PowerShell cmdlet: Get-MpComputerStatus (Figure 9).
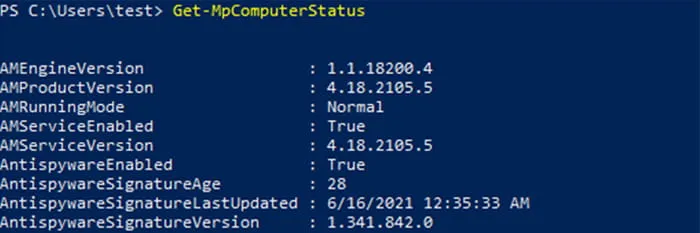
Figure 9: Defender Signature Version PowerShell
Finally, the status of Windows Defender updates can be seen through the SoftwareUpdateClientTelemetry.CheckForUpdates event. As shown in Figure 10, Windows Defender failed to update itself and reported a StatusCode of 0x8024402c. This value is used for network connection failures. (Note: The network connection was disabled for this test.)
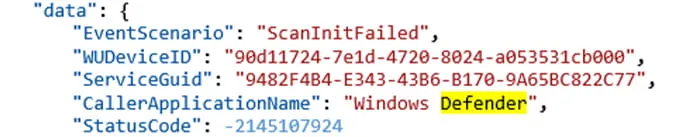
Figure 10: Defender Update Failure