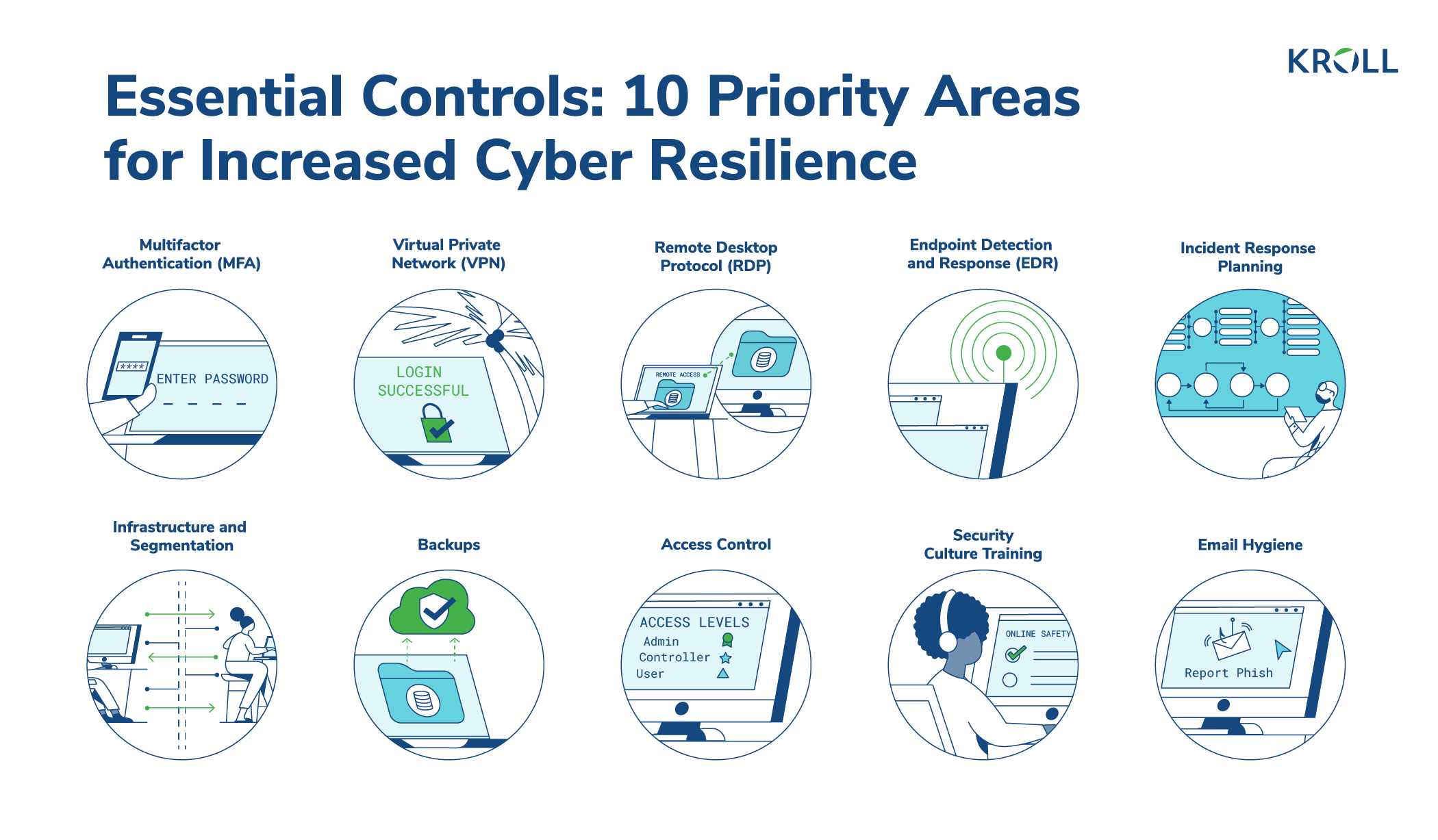
While threat actors continue to vary attack methods, these 10 essential cyber security controls can significantly improve your security posture, therefore making it harder for cyber criminals to compromise your network and increasing your opportunities for cyber insurance coverage. Validated by our seasoned cyber security experts based on frontline expertise and with a thorough review of the expanded questionnaires now requested by most cyber insurance carriers, key takeaways for each of the controls are presented here.
For more details, including hands-on support, get in touch with a Kroll expert today.