
Tue, Jun 15, 2021
2021 Data Breach Outlook – “Under-attacked” Industries Feel the Heat
Industries most impacted in 2019 continued to be hard hit in both 2020 and so far in 2021, including healthcare, education and financial services. However, the greatest percentage increases occurred in industries that had been generally spared in 2019. The overall implication is that data attacks became broader and deeper during the pandemic, a trend that continues during the recovery.
We attribute the rise in data breach notification cases to four trends: the shift to remote work, which has left employees and employers more vulnerable to cybercrime; the evolution of ransomware into data extortion schemes; the rising impact of supply chain attacks; and the combination of stricter privacy regulations with increased awareness of privacy rights. These drivers affect companies in all industries, even the ones that haven’t historically been targets of cyberattacks.
Here we look at drivers of cyberattacks in six of those industries: food and beverage, utilities, construction, entertainment, agriculture and recreation. We then describe actions companies can take to mitigate the risk of data breaches and prepare for a notifiable data breach incident that might occur.
More Industries Vulnerable to Data Breaches
In 2020, Kroll data shows an average 125% growth in breach notification cases for industries which experienced five or more breaches in 2019. We continue to see a surge in the same, moretraditional and regulated, group of industries as we move through 2021.
In contrast, the six other industries—food and beverage, utilities, construction, entertainment, agriculture and recreation—which experienced four or fewer breaches in 2019 according to Kroll data, experienced an average increase of 545% year-over-year (YoY) in 2020. This increased volume of breaches in historically spared industries remains steady in Q1 2021.
“The trend Kroll has identified toward a rise in attacks on previously less targeted industries means that stepping up incident detection and response capabilities for those companies will be extremely important. This is an area where a modest amount of preparation often goes a very long way in avoiding or reducing significant impacts on the business.”– Luke Dembosky, Partner, Debevoise & Plimpton
Increases in Data Breaches Varied by Industry
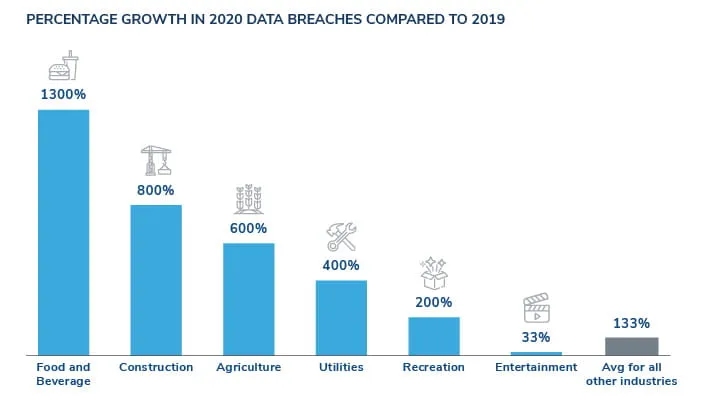
Interestingly, some industries saw a massive increase in data breaches in 2020 as compared to 2019, such as food and beverage, which experienced a 1,300% increase, and construction with an 800% increase. These are eye-popping increases, but it is important to keep them in context. The hardest hit industries experienced many more data breaches than the six industries we are examining here. In 2020, for example, the average number of breaches experienced in historically hard-hit industries was 104, whereas the average number for the group of six historically less-targeted industries was 12.
The hardest hit and heavily-regulated industries—such as financial services and healthcare—are also some of the best prepared to handle data breaches. The historically less affected industries are also less prepared, so it is not surprising that during COVID-19 they would experience dramatic increases in data breaches YoY.
Drivers of Data Breaches Across Industries
Kroll saw the following trends play out across industries during the pandemic:
The Shift to Remote Work Has Left Employees and Employers More Vulnerable to Cybercrime
In most industries, there was an uptick in COVID-19-related "spearphishing" email messages, as well as an increase in malicious activity against platforms adopted for remote work, such as VPN software, remote access infrastructure and cloud solutions like Microsoft Office 365.
The Evolution of Ransomware into Data Extortion Schemes
The economic downturn has triggered an increase in ransomware attacks, which attempt to exfiltrate sensitive data for extortion, with threat actors even taking steps to contact journalists, clients and vendors to pressure victims into paying.
Rising Impact of Supply Chain Attacks
Cybercrime groups have demonstrated considerable operational maturity to not only develop a high rate of zero-day vulnerabilities but also to rapidly exploit security vulnerabilities before patches can be applied. In the last few months, we’ve seen significant impact from large file transfer repositories, email platforms and fundraising software providers that were exploited and the impacts reverberated across thousands of organizations using their solutions.
Stricter Privacy Regulations and Higher Awareness of Privacy Rights
Finally, companies are more likely to report breaches because they have learned—as a result of stricter privacy regulations and greater public awareness around privacy rights—that appropriate responses to data breaches can reduce fines and reputational damage.
Drivers of Data Breaches by Industry
Among these six industries that had the lowest number of data breach notifications in 2019—food and beverage, utilities, construction, entertainment, agriculture and recreation—we saw a 545% increase in notifications from 2019 to 2020. Here, we look closer at these industries to understand the causes of the increase.
Food and Beverage
The food and beverage industry saw a 1300% increase in data breaches in 2020 when compared to 2019, and as of April 2021 the volume of breaches has increased slightly. For example, a large U.S. restaurant chain experienced unauthorized access to their in-house devices and networks, requiring them to notify tens of thousands of customers.
To meet increased demand due to the pandemic, many companies in the food industry operated at full production and were often strained. More importantly, many companies moved to direct-to-consumer e-commerce, which meant collecting and using consumer and credit card data. E-commerce sites are an obvious target of cyberattacks and, according to International Lawyers Network, many in the food and beverage industry “are not sufficiently safeguarded.”
Utilities
The utilities industry saw 400% increase in data breaches in 2020 when compared to 2019, and as of April 2021 the number of breaches has already surpassed 2020 by 25%. For example, a U.S. electric utility company required notifications to be sent to thousands of customers due to an attack that exposed sensitive data in compromised systems.
Utility companies are vulnerable to cyber threats for three reasons, according to McKinsey: the rise in actors targeting utilities, including nation-states, cybercriminals and hacktivists; the “expansive and increasing attack surface, arising from their geographic and organizational complexity;” and the “unique interdependencies between physical and cyber infrastructure, which exposes companies to exploitation.”
According to the American Public Power Association, the COVID-19 pandemic was an opportune time for hackers to attack. A World Economic Forum study noted that “attackers will attempt to exploit the rush to remote systems, understaffed systems and new ways of working.”
Construction
The construction industry saw an 800% increase in data breaches in 2020 when compared to 2019, and this increased volume has remained steady as of April 2021. In one instance, a large North American construction company had to notify hundreds of thousands of customers due to an incident involving a stolen laptop that resulted in unauthorized email access.
“Like many others, the construction sector prioritized business operations in the beginning of the pandemic and some of my clients struggled to scale remote access for staff and contractors, even having to limit who was able to log into the system at certain times of the day.”– Eoin Ó Murchú, Associate Director, Blackrock Expert Services Group, A Kroll Business
Construction and design firms have been innovators around remote work because of the geographical distribution of construction projects. However, when “office staffs started working overwhelmingly from home, security protocols lagged.” Every device, as well as wi-fi at field offices, home offices or coffee shops was an entry point to company data. Construction also calls for a high level of collaboration between firms, so firms are dependent on encryption and other protocols for all participants.
In addition, construction projects are vulnerable to IoT-specific threats. For example, hackers can gain access from wireless sensors deployed in remote locations, or through third-party vendors.
Entertainment
The entertainment industry saw a 33% increase in data breaches in 2020 when compared to 2019, and as of April 2021 the number of breaches has already equaled 2020. One example of this is from a global entertainment company that had to notify thousands of employees after a data security incident disrupted access to their corporate network and exposed personally identifiable information (PII).
High-value targets in the industry are small specialty post-production companies and visual effects (VFX) houses, which handle extremely valuable content. These “rarely have full-time IT staff, let alone in-house content security experts,” according to M&E Journal, whereas big motion picture studios are typically “well-funded and highly resourced.” Targeted attacks are being aimed at these more vulnerable yet highly valuable companies in the production chain.
Agriculture
The agriculture industry saw a 600% increase in data breaches in 2020 compared to 2019, and this increased volume has remained steady as of April 2021. Kroll saw a significant example of this when a large U.S. agricultural equipment distributor became aware of potential unauthorized access to its network, and they had to notify tens of thousands of customers.
Agriculture has gone through digital transformations like most other industries, only to find themselves on the defense. Technology such as mobile apps, smart sensors, cloud computing and drones all rely on the internet, which exposes them to a myriad of complex risks connected to APIs.
Recreation
The recreation industry saw a 200% increase in data breaches in 2020 when compared to 2019, and this increased volume has remained steady as of April 2021. An example of this growth came from a U.S. country club that had to notify thousands of members after their PII was exposed following a series of fraudulent attacks.
According to Villanova’s Center for the Study of Sports Law, there are three types of cyberattacks that sports organizations typically fall victim to: business email compromise (BEC), cyber-enabled fraud and ransomware. Seventy percent of British sports organizations have experienced at least one of these kinds of attacks.
Recommendations
Kroll sees a correlation between the growth in breaches impacting less typical industry targets and a key finding of our State of Incident Response 2021 report—that despite an understanding that data breaches happen and everyone is now a target, 43% of the organizations we interviewed, and more than half of the corporate counsel stakeholders specifically, still felt their organization lacked readiness to notify in the event of a breach.
Our hope is that by highlighting these facts, organizations may more acutely see the importance of solving that problem and having a plan. Given the significant growth in data breach notifications seen in 2020, we strongly recommend organizations take proactive steps to prepare for a notifiable data breach incident. In the long run, it’s likely to minimize regulatory and reputational impact, and may even reduce the impact of class actions.
To help you be better prepare for a breach event when it occurs, we offer the following five recommendations:
Negotiate and Retain Key Vendors to Assist During Incident Response.
Avoid negotiating under the stress of a crisis. Find digital forensics, incident response, breach notification, crisis communication and outside counsel ahead of an incident. Make sure vendors are approved by your cyber insurance policy and able to cover all the regions globally where you have either customers, employees or other critical stakeholder data (it might be worth finding global partners).
Conduct Tabletop Exercises With Your Leadership and Incident Response Vendors So You Are Ready Together for the Inevitable.
Most organizations now have an incident response plan (IRP), but when there’s a compromise, the IRP is dismissed, forgotten or not adequately followed. It’s imperative to conduct regular tabletop exercises with legal and security leadership as well as third-party vendors to build your incident response muscle and increase response speed. Tabletop exercises also help ensure that your vendors are really your partners, you know each other and can work together easily.
Provide Education, Training and Technical Support to Employees.
Ensure that the same standards for data security are applied, regardless of location, by providing mobile workers with straightforward policies and procedures, ensuring security and authentication software is installed on mobile devices and kept up-to-date and offering adequate training and technical support for mobile workers.
Educate employees about appropriate handling and protection of sensitive data. The continuing saga of lost and stolen laptops containing critical information illustrates that corporate policy designed to safeguard portable data only works when employees follow the rules.
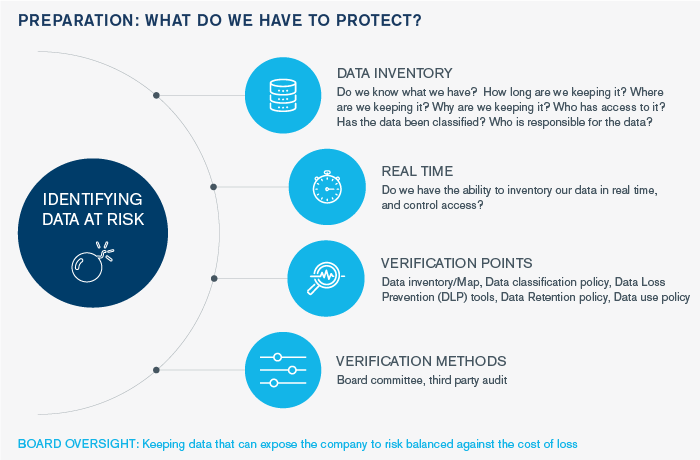
Understand Where Data Lives in Your Organization So You Are Prepared to Not Only Secure and Defend It but Can Access It Quickly in Case It’s Compromised to Help Expedite Regulatory Notice.
Several regulations, like GDPR in Europe and CCPA in the U.S., require organizations to conduct data mapping exercises. This will also help your organization better assess a data diet plan, reducing the number of places where you retain data and the amount of information collected.
Don't Rely on Encryption as Your Only Method of Defense.
Encrypting data in transit and at rest is a best practice, but, when used alone, it can give businesses a false sense of security. Although most state statutes require notification only if a breach compromises unencrypted personal information, hackers can and do break encryption codes.
Final Thoughts
The volume and sophistication of cyberattacks continues to increase, regardless of the regulatory scrutiny placed in any one industry. With most organizations receiving more than 100 threat alerts every day and a reduction of endpoint visibility due to the shift to remote work, the ability to quickly detect and confidently respond to cyber threats has become a difficult challenge for organizations to undertake on their own.
Organizations are strongly encouraged to assess their incident response and breach notification capabilities and consider a 24x7 managed detection and response solution that can augment security capabilities ahead of an incident. Investments in detection and response capability deliver the biggest ROI in security as organizations can stop larger attacks before fully detonating and minimize business interruption.
Cyber and Data Resilience
Incident response, digital forensics, breach notification, security strategy, managed security services, discovery solutions, security transformation.
Breach Notification, Call Centers and Monitoring
Kroll’s data breach notification, call centers and monitoring team brings global breach response expertise to efficiently manage regulatory and reputational needs.
Data Breach Notification Services
Services include drafting communications, full-service mailing, alternate notifications.
Identity Monitoring
Kroll’s unique combination of identity monitoring services can detect more types of identity theft than credit monitoring alone, providing practical help to combat identity theft and fraud.
Credit Monitoring
Credit monitoring can be a powerful tool to offer in the wake of a data breach. Kroll provides a monitoring alert system that’s backed by the expertise of our licensed investigator team.
Identity Theft Restoration
Kroll provides your breach population with direct access to investigative experts for live support and best practice advice, as well as identity restoration should they become victims of identity theft.
Kroll Responder
Stop cyberattacks. Kroll Responder managed detection and response is fueled by seasoned IR experts and frontline threat intelligence to deliver unrivaled response.
Computer Forensics
Kroll's computer forensics experts ensure that no digital evidence is overlooked and assist at any stage of an investigation or litigation, regardless of the number or location of data sources.
Cyber Risk Retainer
Kroll delivers more than a typical incident response retainer—secure a true cyber risk retainer with elite digital forensics and incident response capabilities and maximum flexibility for proactive and notification services.
Insights
Prelude: Crypto Heist Causes HAVOC
by George Glass, Dave Truman , Marc Messer

The Rapid Evolution of CLEARFAKE Delivery
by Ryan Hicks

March Threat Intelligence Spotlight Report
by George Glass, Keith Wojcieszek

2025 Global Business Sentiment Survey: Resilience, Risks, and Preparedness


