Over 55% of organizations want to improve time to containment and incident response automation but more than 45% state inadequacies in detection and response resources.
Kroll, Red Canary and VMware conducted a survey of over 400 information security and 100 legal and compliance leaders from companies with over $500M in annual revenue to capture the current state of incident response from a technical and legal perspective. Our goal was to highlight trends, identify common challenges and understand how organizations are maturing their preparedness, detection and response programs.
Our findings reveal a harrowing scenario with leaders facing obstacles related to internal attitudes toward cyber security, lack of confidence and resources, and remote worker security. Key highlights include:
- Less than half (48%) of organizations conduct regular security readiness exercises with corporate leadership
- In a similar number of organizations (47%) security is perceived as an impediment to business
- Over 90% of respondents are not fully confident in their organization’s ability to identify the root cause of a cyber attack
- Nearly half (46%) of organizations are unable to contain a threat in less than an hour after the initial compromise, and most respondents identified 24/7 detection, response, containment and remediation as a primary goal for 2021
The growing volume and sophistication of attacks doesn’t help alleviate this scenario. When asked about the current threat landscape, the most pressing concerns were:
- Exposure to ransomware attacks (57%)
- Reduction in endpoint visibility due to employees working from home (54%)
- Increased attacks against remote work infrastructure, like RDP and VPN services (53%)
- Hasty migration to cloud services (50%)
Too Many Alerts, Not Enough Triage
Close to 70% of organizations are receiving 100 or more threat alerts every day, but only 20% are investigating more than 20 events per day. Closing the gap between alerts and investigations is key to a more efficient incident response process, but a myriad of challenges stand in the way:
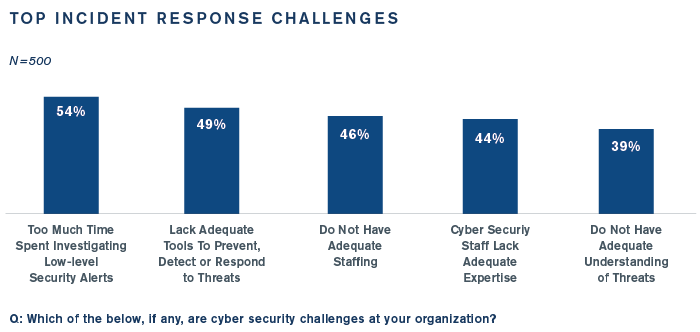
Threat Containment Remains a Struggle
Nearly half (46%) of organizations are unable to contain a threat in less than an hour after initial compromise, and for 23% organizations that reported more than three data compromises in the past 12 months, containment takes at least 12 hours.
Contributing to containment challenges is the difficulty organizations have in acquiring data and intel to investigate incidents:
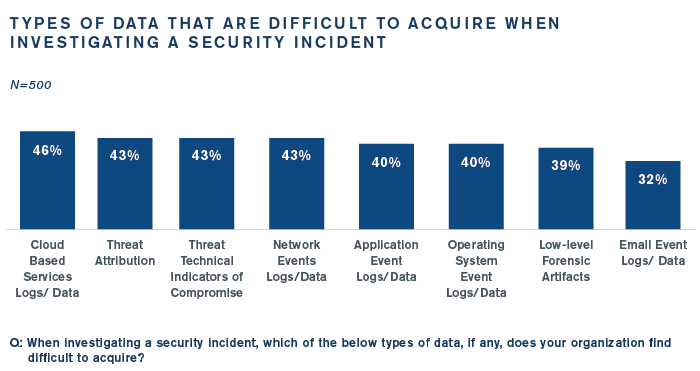
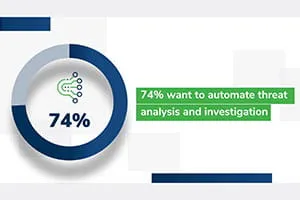
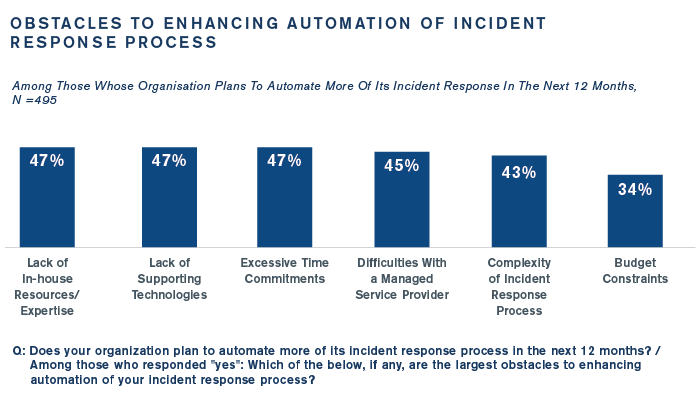
Automation Is a Key Focus, But …
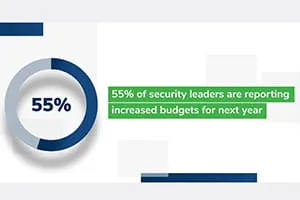
Organizations plan on automating more of their incident response process, but nearly half face headwinds like a lack of in-house expertise (47%) and a lack of supporting technology (47%). See below:
Growing Importance of Managed Detection and Response
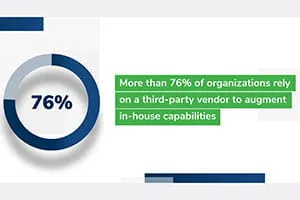
To address these shortcomings, security leaders are increasingly recognizing the benefits of third-party partners that provide managed detection and response. A partner can have an impact across the incident response process, particularly in the areas that security leaders want to improve most:
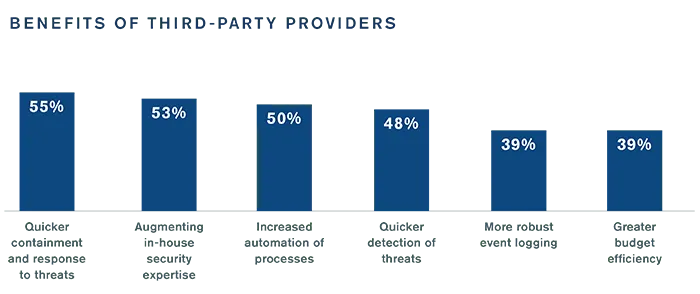
Security leaders are looking for new partners to help leverage these benefits. Four in five (82%) say they will likely work with a new partner to assist with their incident response process, indicating that third parties will continue to play a growing role going forward.
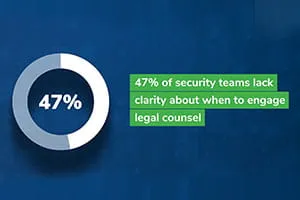
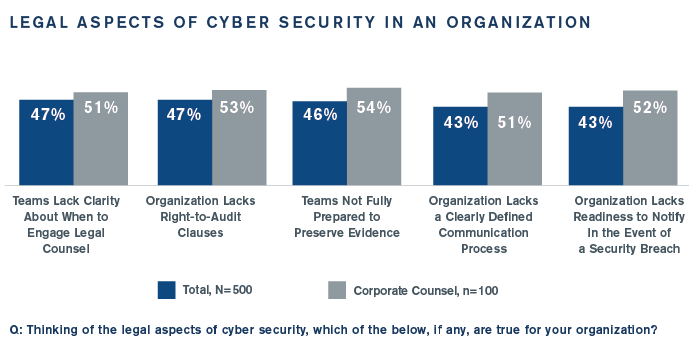
Legal Aspects of Incident Response Cause Issues
The General Counsel’s office is best positioned to act as quarterback in incident response, but many organizations cite numerous legal areas that are challenging, such as knowing when to consult corporate counsel (47%) and a lack of right-to-audit clauses with vendors (47%). Interestingly, corporate counsel expressed higher concern in this area than information security respondents, another indication of the disconnect between departments. See below:
Much, Much More Inside
The full report also covers:
- Are organizations covered by cyber liability insurance?
- How are organizations testing their incident response and recovery capabilities?
- How many organizations rely on third-party IR providers, and what are the main benefits they receive from the partnership?
- What steps are being taken to protect their supply chain?
To gain access to the full results, download the report.