Accountability for Legal Vendor Management
Since the financial crisis, legal departments have experienced their greatest evolution, pushing toward operational excellence and driving greater value from their outside counsel. Although ever-increasing hourly rates started to bring some work in-house, strong reliance remains on outside counsel and alternative legal service providers to deliver the legal services needs of most corporations. Well over 50% of legal department budgets are spent on outside law firms, and they will undoubtedly be the primary service provider to law departments for the foreseeable future.
The relationship between legal departments and their outside counsel is unique and valuable to an enterprise but also challenging from a risk management perspective. This trusted relationship is often tied to a single attorney, rather than a firm, leading to a fluid landscape, where varying caseloads and the mobile nature of attorneys lead to an ever-changing level of engagement across firms. Further complicating this relationship is the fact that many legal departments have obtained exemptions from their corporation’s standard procurement and vendor management processes.
When traditional procurement channels are not engaged, it’s not uncommon to find ownership and accountability of this relationship residing entirely within the legal department. The growth of legal operations has certainly allowed legal departments to decouple the practice of law from the business of law. Although this transition hasn’t always been easy, a set of sourcing best practices and accepted standards has been developed through the hard work and advocacy of organizations like the Corporate Legal Operations Consortium (CLOC) and the Association of Corporate Counsel (ACC).
Outside Counsel Management Guidelines and Cyber Risk Management
Most large legal departments have developed their own vendor management programs, including an Outside Counsel Management (OCM) program that typically includes elements around preferred vendors, alternative fee arrangements, budgeting, invoice review, billing compliance and performance evaluations. Generally, OCM programs are implemented to better define the business relationship with outside counsel, manage costs and drive greater value – all worthy goals. Unfortunately, these programs often lack the risk management components that are typically part of the procurement function, with any cyber risk assessment of outside counsel and other legal vendors often conspicuously missing from the list of OCM activities.
This absence is notable not only because risk management is often a critical step of a traditional procurement process, but also because of the nature of data transferred to outside counsel. In many organizations, this is a treasure trove of highly sensitive and privileged data, representing a relevant and curated list of a company’s litigation, mergers and acquisitions, intellectual property, lobbying activities and more. A 2017 formal opinion from the American Bar Association observed that “[t]he FBI has reported that law firms are often viewed as ‘one-stop shops’ for attackers (with information on multiple clients) and it has seen hundreds of law firms being increasingly targeted by hackers. Law firm breaches have ranged from simple (like those resulting from a lost or stolen laptop or mobile device) to highly sophisticated (like the deep penetration of a law firm network, with access to everything, for a year or more).”1
As demonstrated by the breach of Mossack Fonseca, known colloquially as the Panama Papers or the subsequent Paradise Papers,2 an incident at a single firm can have meaningful impact on hundreds of downstream client organizations. Couple this concentration of sensitive data with increasing global geopolitical tensions, and the need to ensure that organizational data is being appropriately protected is something that can no longer be conveniently ignored. “Law firms are targets for two general reasons:
- they obtain, store and use highly sensitive information about their clients while at times utilizing safeguards to shield that information that may be inferior to those deployed by the client, and
- the information in their possession is more likely to be of interest to a hacker and likely less voluminous than that held by the client.”3
Budgets – particularly those focused on activities generally perceived as cost centers, such as cyber security – continue to shrink. “Since 2007, with the exception of a spike in 2011, the trend for profit margins has been slightly downward over the entire decade.”4 The impact of these budget reductions is seen clearly in recent studies that indicate that law firms have not prioritized or allocated adequate resources to securing their client data:
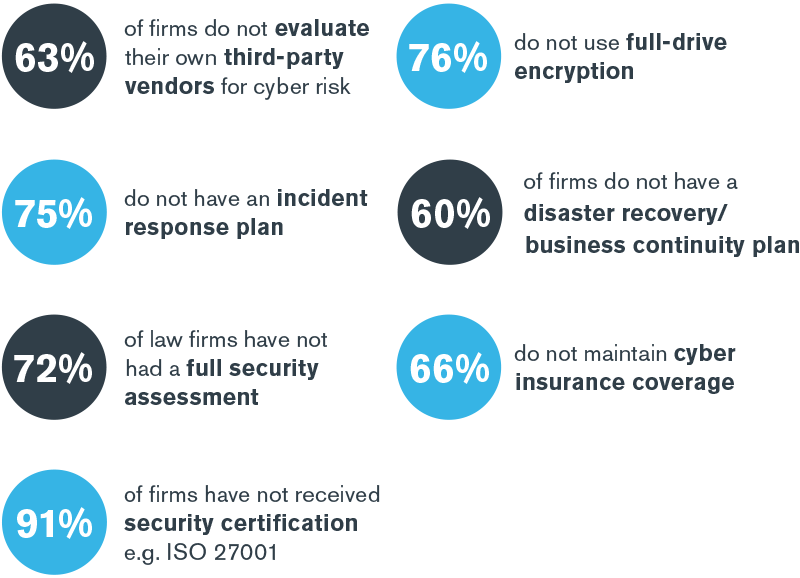
Perhaps a more alarming 2018 statistic from the American Bar Association indicates that “23% of respondents overall reported this year that their firm had experienced a data breach at some time.”7
Why Legal Vendor Cyber Risk Management Is Critical
Although reported cyber security incidents usually focus on loss or theft of data, business interruption poses an equally significant risk to organizations. We have seen several recent examples of this situation befalling large law firms in a public way. In 2017, DLA Piper – one of the world’s largest and most profitable law firms – spent several days at a standstill as a result of a malware incident.8 Not only did this incident cost the firm more than 15,000 hours of overtime for internal information technology staff worldwide, but it was also extremely damaging for the firm. The now infamous image of a whiteboard in the lobby of one DLA office instructing employees to undock and turn off their computers is an unpleasant reminder of this incident.
These risks might manifest in outside counsel, but the ownership of these vendor risks lies squarely with an organization’s general counsel. Although it’s possible to outsource the work or operations, it’s not possible to outsource the risk.
A recent survey of over 130 general counsel from around the world was conducted by Kroll, a division of Duff & Phelps, and LegalWeek.9 This report highlighted the changing role of the general counsel within an organization and assigned responsibility for these – and perhaps all – cyber risks to their domain.
“General counsel are becoming the quarterbacks,” says Jason Smolanoff. “They’re increasingly owning the risk that’s associated with a breach and, as a result, are taking on more and more cyber security responsibilities.”
Ultimate Responsibility
Indeed, ultimate responsibility will fall with the general counsel in many of these cyber-related situations – whether it’s because the breach has regulatory implications, the response is coordinated through an outside firm to provide privilege, or litigation is a possibility. This potential for scrutiny is now being understood by proactive general counsel, who’re realizing that before they coordinate cyber risk responses across the organization, they must ensure their own house is in order.
Download the Report
Sources:
1 https://www.americanbar.org/content/dam/aba/administrative/law-national-security/ABA%20Formal%20Opinion%20477.authcheckdam.pdf
2 https://www.theguardian.com/world/2018/mar/14/mossack-fonseca-shut-down-panama-papers
3 Bradford A. Bleier, Unit Chief to the Cyber National Security Section in the FBI’s Cyber Division, indicated that “[l]aw firms have tremendous concentrations of really critical private information, and breaking into a firm’s computer system is a really optimal way to obtain economic and personal security information.” Ed Finkel, Cyberspace Under Siege, A.B.A. J., Nov. 1, 2010
4 http://www.legalexecutiveinstitute.com/wp-content/uploads/2018/01/2018-Report-on-the-State-of-the-Legal-Market.pdf
5 https://www.americanbar.org/groups/law-practice/publications/techreport/ABATECH-REPORT2018/2018Cybersecurity/
6 LogicForce Q4 2018 - https://www.logicforce.com/2018/11/02/cyber-security-scorecard-q4-2018/
7 https://www.americanbar.org/groups/law-practice/publications/techreport/ABATECH-REPORT2018/2018Cyber security/
8 https://www.biggerlawfirm.com/do-not-fall-down-the-rabbit-hole-of-a-law-firm-data-breach/
9 https://www.kroll.com/en/insights/publications/cyber/legal-week-cyber-report-2018

