The prospect of adding cyber risk management to an Outside Counsel Management (OCM) program can be daunting. Legal operations professionals are quite comfortable enhancing the business and operations of legal departments; however, they may think that engaging in complex cyber risk assessments is better left to their enterprise security teams. Unfortunately, outside counsel firms are generally exempt from traditional vendor procurement or onboarding processes, including engagement of these security teams. Most legal departments view their ability to retain ownership of the legal vendor onboarding process as key to successfully managing these unique outside counsel relationships. Therefore, cyber risk management must be considered as an integral part of the risk management activities within your OCM program.
Beginning Your Journey
The challenges of increasing transparency about cyber risk are similar to those that many legal departments experienced when seeking greater transparency into outside counsel spend. Relationship and engagement managers may regard efforts to understand the cyber risk of their firms as something that hampers their highly trusted and personal relationships. Therefore, obtaining executive and management sponsorship is critical. Clearly communicate that the purpose is to establish a culture of security and to manage cyber risk across the legal vendor portfolio, not to penalize firms. Training attorneys and support staff within the department to understand the goals and objective of the risk management initiative is vital as you begin your initial outreach to firms.
Sample Program Goals and Objectives
Program Objective – Reduce risk in the legal vendor ecosystem by implementing an optimized cyber risk management program:
- Strengthen our law firm relationships through increased security awareness and culture
- Quickly understand risk across our whole legal vendor ecosystem using an inherent risk rating methodology based on data type, quantity, and criticality
- Set clear expectations with vendors about managing our confidential and highly sensitive information.
- Minimize the assessment burden on our law firm partners
- Drive prioritized risk remediation with our most critical and highest risk vendors
Legal Vendor Cyber Risk Management Life Cycle
As you begin to engage your legal vendors on cyber security risks, understanding both the big picture and the steps that you and your firms will need to take together is important.
The third-party cyber risk management life cycle involves five core phases: collect, validate, analyze, remediate and monitor.
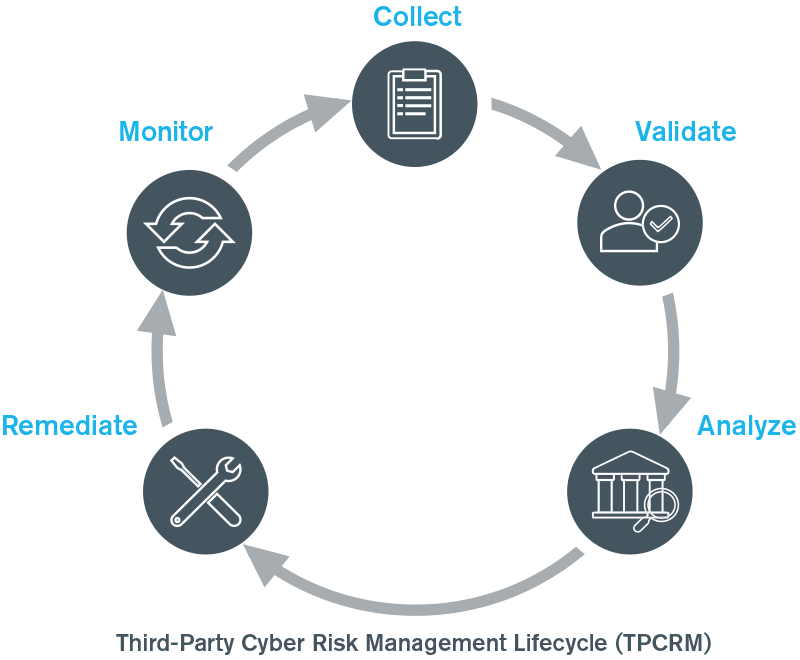
Collect
The first phase of any risk management life cycle is to collect the data you will use to drive the rest of the process. Collecting the right data (i.e., that will help drive risk-based decisions) in an appropriate format is paramount to avoiding the pitfalls associated with data overload. Sending a questionnaire that contains 100 cyber risk questions to 100 vendors will quickly test any team’s ability to review and process thousands of responses.
Well-accepted approaches to collecting this data include leveraging internally developed questionnaires, purchasing standardized assessment questionnaires (e.g., Standardized Information Gathering from Shared Assessments), engaging vendors that specialize in legal vendor third-party risk assessment (such as Duff & Phelps CyberClarity360™), or purchasing a subscription to an outside-in network security rating service (such as SecurityScorecard or BitSight). The decision to build your own assessment vehicle or buy content or services from a vendor is covered in Part 3: Augment Your Legal Vendor Cyber Risk Management Program.
Things to consider for this phase of the life cycle:
- Thoroughness and Focus: Are you obtaining the necessary data to drive the subsequent life cycle phases? Are you collecting extraneous data that’s not being used but instead needs to be reviewed and processed? Reducing the scope to only those elements that you’re actually leveraging can reduce friction for your vendors, increase velocity and reduce risk around collecting and housing sensitive data that isn’t adding value.
- Modality: How will you collect the data? Will you collect it manually using spreadsheets or Word documents via email, or will you use a shared platform like SharePoint? You may even choose to use a platform designed to collect data from hundreds of vendors simultaneously. Consider the human capital required to operate in this modality and ensure that you can support it at the appropriate level.
- Evidence/Collateral: How will you improve the quality of responses? Will you gather supporting collateral or evidence? If so, have you considered the implications around securely transmitting and storing this often sensitive information? Equally important is evaluating whether you have the expertise in-house or need to hire experts to provide a meaningful level of review.
Data Collection: “Outside In” or “Inside Out”?
When collecting information to analyze the security posture of your legal vendors, it is important to consider the primary source from which you will receive this information. As mentioned above, there are multiple collection methods, primarily divided into two categories: “outside-in” and “inside-out.”
- Inside-Out Data Collection
This method delivers data around the vendor’s own view of themselves, usually through self-assessment questionnaires. The unique benefit of this approach is that no one knows more about an organization’s people, policies, procedures and controls than the organizations themselves.
Inside-out data can provide much greater clarity about the organization’s security culture, particularly important in assessing insider threats, and assists in understanding components such as frequency of security practices such as employee training, vulnerability scanning and penetration testing, business continuity and disaster recovery capabilities. This approach can also serve as a proxy of a vendor’s transparency, which is important in a world where it’s not if, but when you are breached.
Inside-out collection methods provide vendors the ability to share rich information about what they have in place today and what they are planning to deploy soon, which have the potential to create an active dialogue between you and your vendors. Finally, when the inside-out view is tied to a specific request developed or deployed or tailored by an organization (such as a questionnaire), it can better reflect the requesting organization’s unique security controls, requirements, and data governance regulations.
Inside-out data collection, specifically self-assessments, does have some draw backs. Certain vendors will paint their security posture in the best possible light and may, even if required to attest to the validity of the information, provide inaccurate or misleading responses. Additionally, some organizations may feel that by sharing this type of sensitive information, they may be putting themselves at risk and thus refuse to participate in this type of assessment or provide such limited data that it becomes minimally useful for the point of the exercise. Some vendors provide only specific information that has been sanitized and streamlined for sharing and draw a hard line in the sand on sharing anything beyond that.
These challenges can be mitigated through positive communication and taking extra steps around requesting and reviewing inside-out assessments. Letting vendors know that this assessment will be viewed as an important part of this relationship, that honesty around security challenges will be met with discussion and not accusations, and that falsehoods will have consequences, will go a long way to ensuring honesty and accuracy in what is shared. Ensuring that any data collected in this mode is shared within a secure medium with limited access and strong controls will help reduce many security concerns.
Some risk assessment solutions, like CyberClarity360, use ‘intelligent’ questionnaires to improve the quality of vendor’s responses, incorporating features such as rules engines to check for inconsistent responses and asking vendors to provide evidence supporting submitted responses.
- Outside-In Data Collection
This method, also known as “Security Risk Scoring” or SRS, is traditionally provided by a vendor who has scanning tools and the capability to review publicly available information to make a prediction on an organization’s cybersecurity posture. Popular vendors in this category include Bitsight, SecurityScorecard and RiskRecon.
The main benefits of this method are speed and scale, allowing faster review of a large amount of vendors. The data is usually already collected and can be validated in the sense that it was observed at a certain date/time on a certain set of unique identifiers (e.g. server names, IP addresses, etc.). Companies that provide this service typically have a score that they apply to their data, based around one or more of the following data elements:
- Website: specifically, how up to date the website software is
- Visibility of networks: looking at how many devices can be accessed from the internet
- History of breaches: leveraging public and private data
- “Unmasked” Accounts: how many account credentials associated with the organization are available on the dark web or were involved in previous breaches
Each of these various “outside-in” providers have taken the time to collect information on as many entities as possible, and since they are viewing publicly accessible data sources, generally do this without the permission, interference, or – in many cases – knowledge of the entities being assessed. This enables them to provide largely unbiased data, though there are some drawbacks to this methodology.
The main challenge of using this type of collection is that it represents a specific data point that has no context from the organizations. The security posture of an organization is not comprised simply of what’s “outside the firewall” or otherwise publicly accessible. Full visibility cannot be achieved by reviewing what is externally available, as controls and protocols operated by a good security team often lie within the organization, working behind a website, and extend beyond the systems and technology themselves.
Additional challenges of this data collection method exist for organizations that are either very large, very small, or relatively new. Very small or new organizations may not have much of a digital footprint, which limits what data an “outside-in” scan can provide. Thus, they may appear to have a stronger posture than they really do, simply because there are no “findings” available. For very large organizations, the opposite can be true. These scans may collect a significant amount of data, resulting in high findings on components such as “attack surface” or other metrics that similarly struggle with accuracy at scale. Another challenge is attribution, where these services often use automated scans to find security weaknesses and it can be difficult to ensure that the weakness found actually belongs to the vendor in question. Finally, each of these vendors present the data and score against their own rubric and with a varying degree of supporting documentation, which makes it difficult to do comparisons across providers.
“Outside-in” versus “inside-out” is an important decision as you collect data to assess your vendors, and one that should be made considering the entirety of your vendor’s security capabilities. To achieve the most holistic view of your vendor’s posture, consider an “inside out” collection, supplemented by “outside in” data to either support or refute the results of the “inside out” self-assessment components. Ultimately, your organization should collect data it can validate and trust to make these important risk-based decisions.
Validate
Validation is often the shortest phase of the life cycle; it also tends to be overlooked. The primary objective of this phase is to ensure that the data you’re going to use to drive the rest of the life cycle is complete, relevant and has a high level of integrity.
If your collection process includes evidence, use the Validate phase to ensure that the evidence provided is both present and relevant. Vendors may utilize a standard set of evidence that they provide all vendor requests, evidence that may be out of date, out of sync with your request or otherwise incorrect. Ensure that you are satisfied with the supporting evidence you receive from vendors. If it’s not relevant or complete, have vendors revisit their submissions.
The goal of the Validate phase is to minimize both downstream frustration and time spent by vendor teams and your own team. If the data provided is insufficient, the Validate phase is the time to address the issue. Once a vendor clears the Validate phase, the working assumption regarding the data is that it’s complete and accurate. This can serve as the underpinnings for any risk-informed decisions taken by your organization in the Analyze, Remediate and Monitor phases.
Analyze
The Analyze phase is one of the most difficult because it requires processing large and often disparate amounts of complex data and deriving meaning at both the micro (individual security controls for individual vendors) and macro (overall performance of your portfolio of vendors) levels. To accomplish this, it is helpful to establish:
- Minimum required controls
- Inherent risk
- Disposition/action required
- Minimum Required Controls: Establishing a baseline of security controls that you expect vendors to have in place will enable you to clearly articulate your expectations in these critical areas and demonstrate a standards-based approach to vendor evaluation.
Typically, minimum controls address the following key areas of cyber hygiene and operations:
- Security policy
- Inventory and device management
- Access control (including passwords)
- Encryption (in transit and at rest)
- Audit and logging capabilities
- Incident response and disaster recovery
- Breach notification
Many organizations struggle to define these controls themselves and turn to an external resource, such as the Center for Internet Security or National Institute of Standards and Technology. You can also develop controls that are tailored to the inherent risk level or type of data your organization is sharing with a given vendor. A more detailed and nuanced discussion on these processes is in Part 3: Augment Your Legal Vendor Cyber Risk Management Program.
Once you establish these minimums, communicating them with your vendor community is important. Having a meaningful, collaborative conversation with a vendor about its risk posture is nearly impossible if you do not first define the metrics against which they are being measured. It’s also important to understand that some vendors will not be able to meet a given set of minimum controls, particularly smaller vendors or those that are not focused on technology. As you will see in the Remediate phase, closing these control gaps will likely take time and significant effort on the part of your vendor. To empower this process, prioritize your internal controls and ensure that the most critical gaps are addressed first.
- Inherent Risk: For many large organizations, the volume of third-party legal vendors can quickly rise into the hundreds, or even thousands. Even well-supported and well-resourced third-party risk programs will be challenged with evaluating risks at this size and scale. To help address this, organizations leverage an inherent risk rating to help categorize vendor risk and focus their limited resources on addressing the highest risk vendors first.
“Inherent risk” is defined as the risk that is present in a vendor when no additional controls are in place. Once controls or remediation have been applied, the term “residual risk” is often applied. Because inherent risk is just that – inherent – it’s a great starting point to identify potentially high-risk relationships and begin to better understand and manage those risks. This process, also known as scoping, generally hinges on several factors relating to your relationship with a given vendor, including:
- Type of data shared
- Amount of data shared
- Type of service provided
- Systems integration/connectivity
Even the most mature organizations struggle with classifying their data against an internal taxonomy, making monitoring data flows with external vendors almost impossible. As a result, some organizations, particularly legal departments evaluating outside counsel, look at annual spend as a proxy to determine inherent risk. While tempting, the ability for spend to be a meaningful risk metric falls short in a few key areas. For example, some firms have a high volume of work, and thus high spend, but may only have access to public data. Conversely, a firm can have a relatively small amount of data and still have a high spend. Finally, spend is a lagging indicator – meaning any risk decisions you make based on spend are always made using old data.
Once you have determined how you are going to categorize the inherent risk of your vendors, you can prioritize analysis of those vendors with the highest risk given your chosen risk categories. This is a critical step in building your cyber risk story – especially if an incident does occur with a vendor while you’re midway through your cyber risk assessment process. In general, if you have defined your risks, sorted your vendors according to those definitions and prioritized the highest risk relationships first, you are in a much stronger position relative to an incident. If you haven’t done any of these things, you are less likely to get the benefit of the doubt from your board, from regulators or in litigation.
Inherent Risk Approach for Legal Vendors
The inherent risk approach for assessing the legal vendor portfolio may not be optimal. The unique and fluid nature of the relationship with outside counsel could easily shift utilization across law firms. A new discovery by a business unit could force an organization to quickly share significant sensitive information with a firm that had previously been used only on a small scale or for less sensitive matters. Such circumstances could completely change the risk profile of the firm, often without any trigger to reassess the risk. An inherent risk approach would likely exclude such a firm during initial review. Accordingly, when assessing legal vendors, it is more important to take a comprehensive approach and to understand the risk profile of all firms at a given time.
- Disposition/Action Required: The outcome of the Analyze phase should provide clear next actions for the vendor in question. Typical outcomes for this phase of the risk management life cycle include a variation on one of the following dispositions:
- Accept all risks – no action required on behalf of the vendor
- Conditional acceptance – some actions required by the vendor
- Do not accept – alter or terminate relationship with vendor
Remediate
Of all phases, Remediate is not only the most critical but also the most often overlooked. In this phase, you use the data you have collected, validated and analyzed to drive improvements into your portfolio or implement your own internal compensating controls to better manage the risks surfaced through this process.
Many organizations are hesitant to meaningfully engage in this phase because of one or more of the following:
- Responsibility for remediation rests solely with vendors
- Potential exposure to downstream liability exists
- They have insufficient resources or technical expertise to provide remediation guidance
- The sheer volume of vendors and control gaps is overwhelming
While these hurdles are common for organizations, if your goal is to meaningfully manage and mitigate risk in your vendor portfolio, they are critical to overcome.
- Prioritize Gaps: Considering every control gap as an equal risk is not productive, nor is asking a vendor with multiple control gaps to remediate them all concurrently. Instead, work to prioritize your vendors against your inherent risk ratings. Address the highest risk vendors first, and focus on their most critical risk control gaps.
- Communicate: Working with your internal vendor relationship managers and points of contact to share the findings from your assessment is essential, including the risk and impact of any gaps and desired remediation activities. Generally, the more collaborative and proactive you can make this exercise, the better the likely outcome of the overall effort. Recall that the objective is not to be punitive toward your vendors but rather to identify and better manage risk. Many, if not most, vendors will require a significant investment of resources to remediate gaps.
The mode of communication should be appropriate to the risk. For high-risk vendors or those with high-risk control gaps, connecting directly via a phone call, web conference or in person visit is more effective to ensure they fully understand the scope of your expectations and have a chance to ask any clarifying questions. For low-risk vendors or those with low-risk control gaps, use of a more automated mode of communication is likely appropriate.
- Negotiate: The activities to close any gaps with vendors often represent a significant project. Each legal vendor has a unique cyber risk story. The larger and more mature vendors are better able to respond to remediation activities in a reasonable manner. Smaller or less mature vendors are simply unable to devote adequate resources to addressing cyber risk. Therefore, a flexible approach is needed to achieve an improved posture across the portfolio.
Vendors should be allowed to determine the remediation activity and time frame because their priorities will be driven largely by their own commercial and business goals. However, you can set expectations to help guide both the vendor and your own internal resources to an agreement that meets the needs of both.
Monitor
Once a remediation plan has been established and work is underway, continued diligence is necessary to ensure the vendor delivers on its promises. Best practices include requesting regular updates regarding progress on the agreed-upon plan.
Beyond monitoring compliance against agreed-upon remediation plans, it is a best practice to monitor vendors for news or information that may materially impact your relationship, present additional risks or exacerbate existing risks. You can accomplish this additional monitoring through a range of available services, including traditional negative news feeds.
Other Considerations
In addition to the phases of the third-party risk management life cycle, you should consider several other elements as you begin to build your program.
Risk management is not a one-time activity. While some components of risk management certainly reflect a point in time, the need to continually reassess risks is driven by many factors, including:
- Continuously evolving threat landscape
- Dynamic relationships with changing risk profiles
- Internal changes to technology, sourcing and data utilization
- Increasing state and federal regulatory compliance obligations
To account for each of these challenging elements, you need to create a program that is sustainable, scalable and defensible. This means that you will have ongoing program activity and should ensure that the associated cost and efforts are understood and supported by the highest levels of leadership within your organization.
Conclusion
While the creation of a Legal Vendor Cyber Risk Management program is not a small undertaking, it’s critically important given the significant reliance on your external legal vendor ecosystem to deliver legal services. Ensuring that your vendors understand not only their role in maintaining a secure posture but also the importance of transparency and collaboration through the required diligence is paramount to appropriately mitigating risk. By implementing the steps discussed in this guide, you will make meaningful progress toward both maturing your approach to managing cyber risk within your vendor ecosystem and engendering material progress in enlisting your vendors to partner with you on these efforts.
Download the Report
