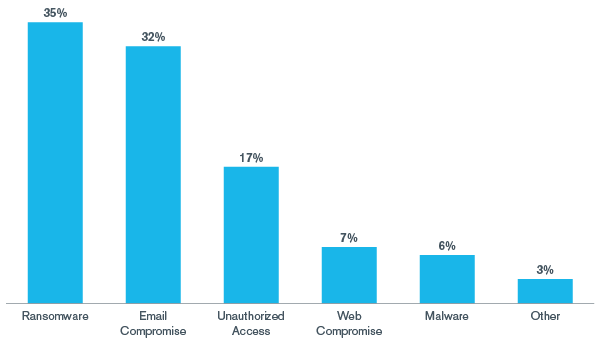
Ransomware was the most observed threat year to date (YTD) across Kroll’s intake of cyber incident response cases, accounting for over one-third of all cases as of September 1, 2020.
Ryuk and Sodinokibi, perennially the most observed variants in Kroll’s cases, have been joined by Maze as the top three ransomware variants so far in 2020. After launching several high-profile attacks earlier in 2020, the actors behind Ryuk ransomware seem to have gone on a hiatus near the end of Q2. However, in Kroll’s experience, crimeware and their developers often have periods where they go dormant or spend time re-tooling, followed by a resurgence of activity.
This appears to be the case as Kroll has noted a spike in Ryuk-related investigations the last two weeks of September, while a large US hospital system has also reportedly become a Ryuk victim as of September 28. Recently, open and closed sources have speculated that Ryuk has emerged with a new identity: Conti. Based on similarities in code, Conti ransomware is believed to be a descendent or similar variant of Ryuk ransomware, and Kroll’s Cyber Threat Intelligence team has observed that operators have been hosting a victim “shaming” blog since August 2020.
While ransomware figures prominently in myriad security alerts and media reports, business email compromise (BEC) remains a top threat for organizations worldwide with its associated risks like wire fraud and misdirected payroll. BEC was close behind ransomware in Kroll’s threat list, involved in 32% of Kroll’s cases (Figure 1).
Data Exfiltration Risk in Nearly Half of All Ransomware Incidents
Ransomware actors have been plaguing victims by encrypting files, paralyzing operations and demanding increasingly exorbitant ransoms. However, many are also exfiltrating data and threatening publication on the dark web, a relatively new tactic that gained momentum in early 2020. Since Kroll first published on this new shaming technique in February 2020, many more variants have added exfiltration and publication to their bag of tricks. Nearly half (42%) of Kroll’s cases with a known ransomware variant are connected to a ransomware group actively exfiltrating and publishing victim data.
In addition, groups like Maze and Sodinokibi that pioneered the shaming sites have evolved their capabilities; Maze now boasts of a “cartel” that allows other ransomware variants to cross-post victims on their shaming site. In May 2020, Sodinokibi added an auction site to their shaming site where they offer data to the highest bidder.
While actors say they will delete data upon payment of the ransom, recent events belie that claim. Devon Ackerman, Managing Director and Head of Incident Response, North America, has learned that rogue members of ransomware groups have approached and demanded a second payment from at least two victims who had already paid a ransom. When one of the victims balked at paying the second time, the data, which was supposed to be destroyed upon the first payment, ended up on an actor-controlled site.
Primary Precursors: Open RDP, Phishing, Vulnerability Exploits And Account Takeovers
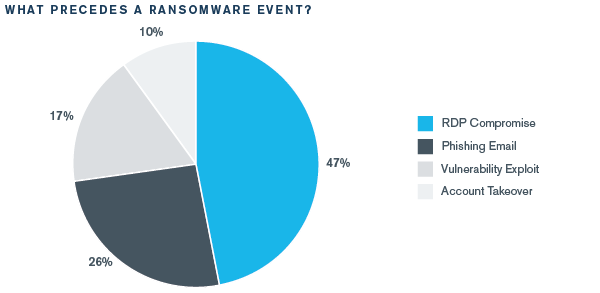
Threat actors in nearly half (47%) of Kroll’s ransomware cases leveraged open remote desktop protocol (RDP) and Microsoft’s proprietary network communications protocol and more than a quarter (26%) cases were traced back to a phishing email. Vulnerability exploits (17%), including but not limited to Citrix NetScaler CVE-2019-19781 and Pulse VPN CVE-2019-11510, and account takeovers (10%) rounded out the primary ransomware precursors (Figure 2).
Who’s Being Most Targeted?
While ransomware strikes organizations of all sizes across every sector, Kroll has observed three sectors being struck especially hard this year: professional services, healthcare, and technology and telecommunications. Notwithstanding some threat actor group claims that they would avoid targeting healthcare organizations during COVID-19, others are either not so civic-minded or have done so unintentionally.
This seems to have been the case last week when threat actors thought they were targeting a university in Germany, whereas, in reality, they struck an affiliated hospital system. Open-source reporting notes the threat actors exploited a VPN vulnerability (#2 in Kroll’s list of ransomware precursors) to gain initial access to the system.
How to Prevent or Mitigate the Harms of Ransomware?
While no organization can prevent becoming a target, strategies exist for making it harder for threat actors to gain access and wreak damage. By addressing 14 key risk areas identified by Kroll through its frontline casework, organizations stand a better chance of proactively preventing unauthorized access and mitigating harm. The growing number of attacks built on ransomware-as-a-service variants and the aggregation of threat actors into cybercriminal cartels makes ransomware preparedness a priority for every organization.