Kroll experts have noticed an increase in distributed denial of service (DDoS) attacks by cybercriminals seeking to turn a profit in two distinct incident types. First, many ransomware operators are now threatening and conducting DDoS attacks as an additional pressure tactic during the ransom negotiation process. Second, also known as ransom denial of service (RDoS), attackers threaten DDoS attacks that will take down an organization’s public-facing services unless a ransom is paid.
What Is DDoS?
DDoS attacks are designed to take advantage of bottlenecks within an organization’s systems. If a website or other internet-facing service is flooded with more data, traffic or requests than it can handle, the system may be unable to respond to legitimate requests and ultimately crash. Attackers often use this method as a means of causing confusion within an organization’s systems to prevent regular business activity and distract employees while data is exfiltrated.
Attacker Insights and Motivations
Multiple ransomware gangs have added DDoS attacks as another pressure tactic during the ransom negotiation process. Figure 1 highlights a DDoS threat posted to the Avaddon ransomware group’s actor-controlled site. Such activity frequently occurs when negotiation discussions stall as a means for the ransomware gangs to force the victim to resume discussions.
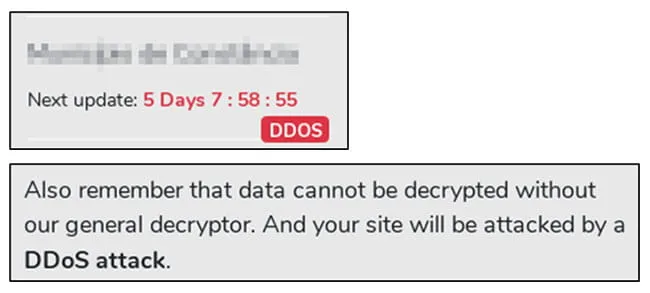
Figure 1: Avaddon DDoS Threats
An RDoS attack adds an extortion element to a standard DDoS attack. In these instances, a cybercriminal may threaten to perform a DDoS attack against an organization unless a ransom is paid. In these scenarios, the actors will perform a “teaser” DDoS attack, sending anywhere from 50–100 gigabytes per second (Gbps) against an IP address associated with the target to prove their ability to perform the attack.
After the initial “teaser” attack, threat actors will often threaten higher-volume attacks that may cause more damage to public-facing services unless the ransom is paid. In order to provide legitimacy to this threat, actors may masquerade as well-known advanced persistent threat (APT) groups. In reality, the groups sending the extortion letters commonly lack the ability to actually carry out the DDoS attacks they threaten. These letters typically come in waves following news reports of major DDoS attacks or the discovery of a new vector for carrying out DDoS attacks. Sometimes, the attacker may not carry out the follow-on attack, even if the target does not pay the ransom demand.
On occasion, an organization may not experience a “teaser” attack at all but rather just receive a letter threatening such activity. Receiving an RDoS extortion threat via letter does not mean that an organization is under threat of an attack. In fact, most legitimate RDoS attackers work under the radar and will not provide any warning before carrying out their sample attack.
RDoS Attack Patterns
Some common features of attempted RDoS attacks identified by Kroll analysts include:
- Protocols
RDoS attackers use a variety of different network protocols to flood a target system with traffic. These attacks can take advantage of DDoS amplification, where spoofed traffic sent to a particular service results in much larger responses being sent to the target system. - Volume
RDoS attacks can achieve high bandwidths of malicious traffic. The largest attack observed by Kroll reached a peak of approximately just under 200 Gbps. - Targets
The IP addresses targeted in these attacks are located in different places. Often, these are systems with a single public-facing SSH, RDP, NetBIOS, or HTTP port open to the internet. - Botnets
DDoS attackers commonly use a network of compromised computers to generate the malicious traffic in their attacks. In general, many of these systems are internet of things (IoT) devices and other computers that are compromised due to their use of weak usernames and passwords.
These RDoS attacks can easily take down under-protected public-facing services. However, a DDoS mitigation solution with robust traffic scrubbing capabilities can easily handle attacks of this volume.
Illustrative Case Study
In a recent Kroll engagement, a victim was the target of an RDoS attack performed by a group claiming to be an advanced persistent threat (APT) group. The DDoS attack took down the company’s internet-facing assets.
A few employees received a ransom note via email that had supposedly come from the criminals, with instructions on when and how the company could make payments to prevent a future attack from occurring.
The organization reached out to Kroll to help with managing the incident. Kroll analysts took several steps to improve the company’s security posture and protection against DDoS attacks:
- Compromise Assessment
DDoS attacks commonly originate from outside the victim’s network and may not indicate the organization had been compromised, but it’s important to confirm whether the criminals had established any sort of foothold within the impacted organization. - Gap Analysis
Kroll analysts began with an analysis of the organization’s defenses against different types of DDoS events. This included evaluating the current protective technologies that were in place, reviewing the company’s overall network architecture, and identifying vulnerabilities that could be exploited by a DDoS attacker. - Risk management Recommendations
Based on the results of the gap analysis, Kroll analysts provided recommendations on steps that the organization should take to both mitigate the short-term threat of the RDoS attack and manage their cyber security risks in general. - Threat Intelligence Research
Kroll’s threat intelligence research helped the organization better understand the common tactics, techniques and procedures used by the criminal group and assess which other threats posed the highest risk, based on the organization’s footprint.
Kroll Experts Corner – Protecting Against DDoS Attacks
The following recommendations, provided by Kroll expert James McLeary, should be taken into consideration to protect against the threat of DDoS attacks:
- Consider implementation of DDoS scrubbing (cloud-based DDoS mitigation) solutions to give additional protection but ensure multi-layered overall approach across cloud protection, CDN, DNS and application-based appliances
- Contact your incident response partners and consider methods such as rate limiting, port blocking and blocking specific servers, if under such an attack.
- Provide indicators of compromise to your internet service providers (ISPs) so they can also action responsive measures
- Ensure good cyber hygiene in your environment—identify prioritized assets that require extra protection and ensure your vulnerability and patch management is up to date
- Develop a DDOS incident response playbook and test it to solidify what to do during detection, response and recovery
- Consider the use of out-of-band communication channels for crisis handling that do not rely on ordinary corporate infrastructure. For example, if your corporate email, messaging and Active Directory services are affected by DDoS, the team can quickly switch to using temporary webmail, instant messaging or group chat applications, whilst being aware of the risks that this may pose.
To adequately protect your organization from a DDoS attack, it is important to implement good cyber hygiene to ensure you’re covered. In the event of an attack, Kroll experts can help respond. For further guidance, contact a Kroll expert at one of our 24x7 cyber incident response hotlines or connect with us through our Contact Us page.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.



