Article 3 of series Sophisticated Anti-Forensics Tactics and How to Spot Them: Timestomping
Digital forensics analysts can locate and identify timestomping using a combination of Kroll Artifact Parser and Extractor (KAPE), MFTECmd and Timeline Explorer. KAPE uses Targets and Modules to acquire and process artifacts, respectively, into easily digestible output for examiners to analyze. Specifically, the $MFT Target can be leveraged to acquire the $MFT, while the MFTECmd_$MFT Module can parse the $MFT to generate CSV output, which can be ingested into Timeline Explorer for analysis.
After the necessary tools are downloaded and extracted, run gkape.exe (Figure 1).
Figure 1 – KAPE folder extracted – Run gkape.exe
Once gkape is open, KAPE Targets can be enabled to select the operating system drive where artifacts of the drive are dumped. In order to parse the $MFT, KAPE must collect the file from the operating system partition where it is stored. This is considered the target source (C:\). Next, indicate where the $MFT should be placed for further analysis and parsing. This is the target destination (C:\Tutorial/tout).
Once the $MFT has been selected, KAPE Modules, located on the right side of the KAPE interface, can be utilized to parse the file using a specified command line tool. KAPE Modules can leverage nearly any command line tool, regardless of its intended purpose. KAPE Modules have been crafted by the community to provide a one-click solution for the most commonly applicable use-case of a given tool.
First, specify the Module destination (D:\Tutorial\mout). Next, leverage the MFTECMD_$MFT Module, which specifically runs MFTECmd to parse the $MFT artifact that was pulled using the $MFT Target. Acquiring and parsing the $MFT using MFTECmd can be done seamlessly using KAPE (Figure 2).
In this scenario, the following variables are used:
- Target source: C:\
- Target destination: D:\Tutorial\tout
- Module destination: D:\Tutorial\mout
- Target: $MFT
- Module: MFTECmd_MFT
- Debug messages
Once these variables are set within gkape, the command can be executed successfully. This will provide CSV output containing the contents of the parsed $MFT. Debugging messages is recommended for troubleshooting purposes.
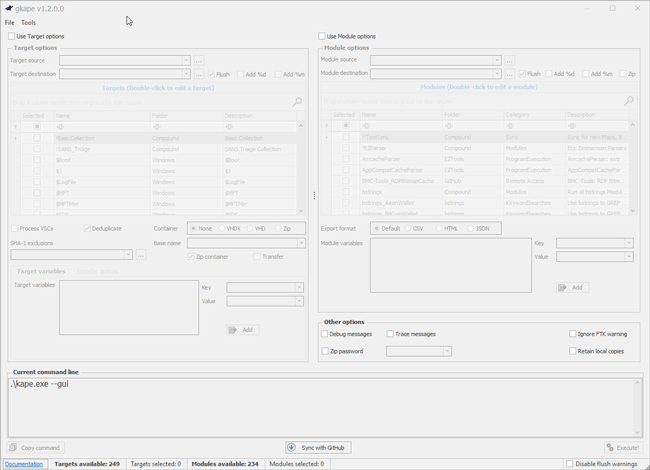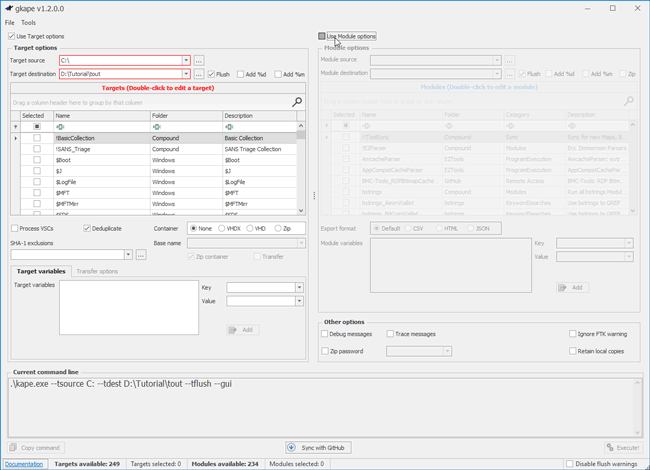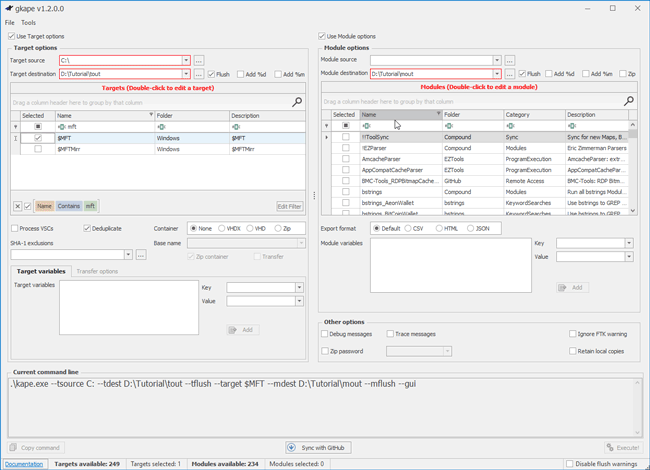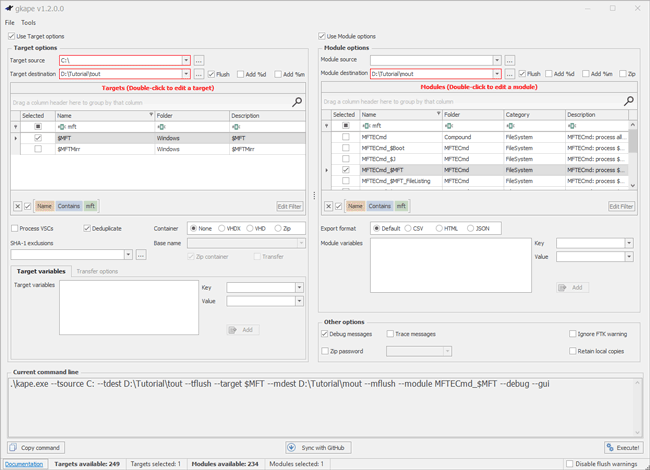
Figure 2 – Using KAPE to collect and parse artifacts
Once KAPE has finished processing, the console window should look like Figure 3.
Figure 3 – kape.exe console window output
Identifying Indicators of Timestomping in Timeline Explorer
Created (0x10)/Created (0x30), SI<FN, u Sec Zeros, Copied Fields
The parsed $MFT CSV output can be located in the FileSystem subfolder within the user-defined Module destination folder, and the output can be loaded by dragging and dropping the CSV into Timeline Explorer. Files that were timestomped previously with NewFileTime can be located a number of ways:
- Searching for the file name (if known)
- Filtering on the file extension (Figure 4)
- Sorting on the Created (0x10)/Created (0x30) timestamps
- Created (0x10) is the Standard Information (SI) creation timestamp. This can be modified by user level processes, for example, timestomping.
- Created (0x30) is the FileName (FN) creation timestamp. This can only be modified by the kernel, or tools leveraging the kernel, which is a privileged and restricted portion of the operating system that contains software to interface directly with hardware peripherals, implement security controls and schedule and control processes acting on behalf of a user.
- The presence of a Created (0x30) timestamp can be useful in spotting discrepancies between the two timestamp values.
- Filtering on the SI<FN (Standard Information < FileName Attribute), u Sec Zeros or Copied fields.
- The SI<FN field shows files where the Standard Information Attribute (0x10) is earlier than the FileName Attribute (0x30). Kroll's observations over numerous engagements relating to timestomping indicate threat actors are more likely to timestomp files into the past, rather than the future, in order to hide timestomped files among benign files from prior to the incident timeframe to confuse analysts.
- The u Sec Zeroes shows files where milliseconds are zeroed out. Please note that this is simply a potential indicator for timestomping. Kroll has observed multiple instances where the subseconds on application files are zeroed out with no suspicion of timestomping. As always, the totality of the circumstances will come into play when determining whether timestomping is performed by threat actors.
- The Copied field shows whether the Last Modified timestamp occurs before the Created timestamp, which is indicative of a file copy event.

Figure 4 – Filtering on “.jpg” and “Desktop” in Timeline Explorer
Several relevant artifacts to look for:
- Created (0x10) timestamp showing .0000000 milliseconds appended to the end of the file’s timestamp
- Created (0x30) timestamp having an entry in the MFTECmd CSV output
Two Key Indicators for Identifying Timestomping in the parsed $MFT
There are two important factors when identifying a timestomped file within the $MFT after it has been parsed using MFTECmd. First, if timestomping has occurred, the Created (0x10) timestamp’s subseconds value would always appear to be zeroed out (.0000000). Timestomping tools do not appear to be able to allow for the end-user to customize the subseconds value(s) of a file’s timestamp(s). Kroll has found any alteration to the timestamps appear to zero out the subsecond values.
Coupled with this indicator, if a file has been timestomped, there will always be a value in the 0x30 column. This is because if the values in the Created (0x10) and Created (0x30) match, the Created (0x30) cell will be empty. If there is a value within the Created (0x30) cell, that timestamp must be different from the Created (0x10) timestamp. This allows an analyst to quickly rule out files that have not been timestomped by filtering based on the Created (0x30) cell values (Figure 5).
It should be noted that this convenience is unique to Eric Zimmerman’s MFTECmd tool output and not the $MFT itself. Also note that there are instances where files can have both zeroed out Created (0x10) subseconds as well as a value in the Created (0x30) cell. In this scenario, an expert should consider the totality of the circumstances when attempting to identify files that may have been tampered with by a threat actor.
Figure 5 – Comparing the “Created 0x10” and “Created 0x30” timestamps in Timeline Explorer
MFTECmd adds three fields to the parsed $MFT output. These fields, SI<FN, u Sec Zeros and Copied. SI<FN and u Sec Zeros, are relevant for identifying timestomping. Figures 6 and 7 show examples of these fields in action. (The “Copied” field will be covered in the future.)
Figure 6 – Files with SI<FN field checked in Timeline Explorer
Please note, SI<FN assumes that files have been timestomped into the past. This translates to a 0x10 timestamp being earlier than a 0x30 timestamp. This logic will not notice the rare instance that a file is timestomped into the future, which should arguably stand out on its own accord.
Figure 7 – Files with u Sec Zeroes field checked in Timeline Explorer
KAPE and MFTECmd, together with Timeline Explorer, can serve as tools for digital forensics investigators looking to identify timestomping. KAPE provides a quick, digestible solution for acquiring and parsing artifacts, and MFTECmd allows the $MFT to be parsed to generate a CSV output that can be ingested into Timeline Explorer for analysis. Although there are many ways to identify this anti-forensic tactic, using a combination of KAPE, MFTECmd and Timeline Explorer is a quick and efficient strategy for forensic experts.
Related Articles











