Kroll has recently observed a new malware strain called “Bumblebee” operating as a loader, delivered via phishing email, in order to deploy additional payloads for use in ransomware operations.
The malware takes its name from the unique user-agent (since changed), which it used to connect to command and control (C2) servers. It was first reported by Google's Threat Analysis Group (TAG) in March 2022, with the first sample submitted to VirusTotal on March 1.
Bumblebee operates in a similar way to Emotet or IcedID, in that it deploys additional payloads, such as Cobalt Strike, which are frequently used in ransomware operations. The operators of Bumblebee, dubbed EXOTIC LILY by TAG—who identified this group to have been operating since at least September 2021—have been linked with the Conti ransomware group. Proofpoint tracks the two activity clusters distributing Bumblebee as TA578 and TA579.
Kroll has correlated known Bumblebee C2 servers to prior Ryuk and Conti shared infrastructure, as well as IcedID, a trojan which has been used in Quantum Locker ransomware operations.
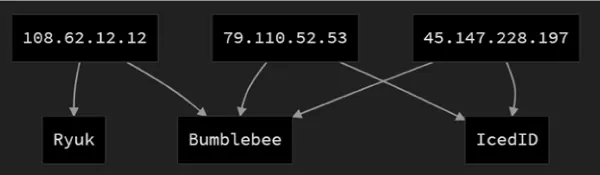
Figure 1 - Overlap of Bumblebee infrastructure to Ryuk and IcedID. Sources: Triage.io, CIRCL, Intel471
Kroll's digital forensics and incident response have recently observed Bumblebee used as an initial infection vector to a Quantum Locker ransomware attack, with the time to ransomware execution less than 22 hours after initial infection. The Bumblebee loader downloaded Cobalt Strike, which was used to stage additional tooling for network reconnaissance, and culminated in a ransomware infection.
Delivery
During our investigation of the Quantum Locker ransomware case, we observed a BumbleBee payload delivered via an .iso file downloaded from a Google storage service. The phishing lure was delivered via a web site contact form in which the threat actors, purporting to be a third party claiming the victim organization had infringed their copyrighted materials—a tactic we have seen used by actors to deliver IcedID previously.
In our open-source investigation, we observed that the group has used the following methods to deliver the malware:
- Phishing email with link to file sharing service offering a download .zip of .iso container, which contains .lnk and .dll files. (Some also contained a .html attachment as an additional redirect lure.)
- Phishing emails with directly attached .iso containers.
- Email thread hijacking using both of the above methods.
- Excel .xlsb files downloaded from Microsoft OneDrive containing Excel 4.0 macros to download and install Bumblebee.
For methods 1 to 3, upon opening the .iso container, .lnk and .dll files are made available. The .lnk is designed to lure the victim into double clicking, thus executing the .dll and downloading Bumblebee. Persistence is achieved via VBS script initiated by a scheduled task.
Figure 2 below shows the process tree of the Bumblebee 64-bit .dll execution on a Windows 10 sandbox. Note the immediate communication with C2.
Figure 2 - Sandbox Analysis of the Bumblebee executable. (Source: Kroll)
Click the image to view in full screen.
Initially, detections from anti-virus vendors for Bumblebee’s .lnk and .iso files were poor, demonstrating the effectiveness of this evasion technique. Executables are detected as “Ursnif” by a number of AV vendors.
Capability
Bumblebee has a number of advanced features and capabilities which we assess are still under heavy development. To date, these are:
- Windows Management Instrumentation (WMI) usage to gather system information
- Execution of further commands via PowerShell and Wscript
- Process injection
- RC4 encryption of command-and-control communication
- Persistence mechanism via VBS script and scheduled task
In addition to the Cobalt Strike payload we have seen Bumblebee deploy it has also downloaded, Meterpreter, and Sliver after successful installation, according to Proofpoint.
Development
While the malware has only been circulated for two months, it has undergone significant development and changes in that time.
Google’s TAG notes that the group's campaigns have been growing in size and target scope:
“At the peak of EXOTIC LILY’s activity, we estimate they were sending more than 5,000 emails a day, to as many as 650 targeted organizations globally. Up until November 2021, the group seemed to be targeting specific industries such as IT, cybersecurity and health care. More recently, we have observed them attacking a wide variety of organizations and industries, with less specific focus.”
The initial run of Bumblebee gained its name from the “Bumblebee” user-agent string, which is used to communicate system information to C2 servers and did not feature the 10-character RC4 encryption passphrase that later versions have. The RC4 passphrase also changes for each web request made.
Operating as an initial access broker, the developers behind Bumblebee have been experimenting with various techniques and targets in order to gauge the effectiveness of their campaigns:
- EXOTIC LILY began exploitation of the MSHTML vulnerability, CVE-2021-40444, before switching to Bumblebee campaigns.
- Development and inclusion of anti-sandbox and anti-analysis checks, using capabilities developed as part of the “al-khaser” anti-analysis project.
- Support for multiple C2 addresses, for redundancy.
- Use of various file sharing sites, typically allowed by corporate web filtering:
- WeTransfer
- TransferNow
- Google Drive
- Microsoft OneDrive
Although the malware is relatively new, significant development effort has been expended on this malware strain, and it is interesting to note that the operators appear to have also quickly pivoted to delivering malware bundled inside .iso containers. They have also used web contact forms as a way of bypassing inline email security products, a tactic used to deliver both IcedID and BazarLoader in the past.
We assess that, due to the relatively large quantities of spam detected by Google TAG, the rapid development evidenced in the analysis we have conducted on publicly submitted samples, and the use of Bumblebee in a successful Quantum Locker ransomware attack, the actors operating Bumblebee are highly motivated and will likely continue development and attacks in the near term.
Recommendations
- Consider deploying endpoint detection and response (EDR) and next-generation antivirus (NGAV) to all devices within your environments to allow for early detection. Detection opportunities include:
- .vbs execution as a scheduled task.
- .dll execution following an ISO container being mounted.
- Review inbound email policy and consider quarantining attachments from unknown or untrusted senders.
- Block users from opening non-standard files such as : Bumblebee has been observed using .iso, .dll, and .vbs files. Consider also blocking; .jar, .js, .lib, .mst, .msp, .bat, .cmd, .com, .cpl, .msi, .msix.
- Run awareness campaigns for these latest infection methods, including the use of legitimate file sharing sites serving .iso files.


