Watch the full webinar and download the slides: Effective Business Email Compromise and Ransomware Mitigation
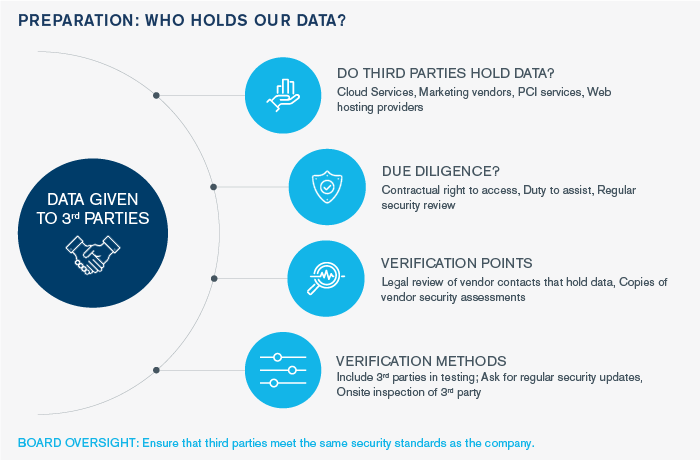
It is crucial for security and privacy leaders to monitor and update contracts with third-party vendors to protect their organizations from data breaches. Very often, a data incident originates with a vendor whose security has not been validated due to a lack of legal authority, which should be present in the contract. Clauses such as a contractual right to access and a duty to assist in security reviews are fundamental to ensure a healthy third-party cyber risk management program. In doing so, an organization can audit and ensure the safety of the data being kept by a third-party.
How to keep track of the data your third parties have?
It is important to hold your vendors to the same security standard to which you hold your own organization. Monitoring and maintaining the data that your vendor holds should be managed the same way as your internal data inventory. Ensure you’re taking the following steps when keeping track of your third-party data:
- Review your vendor contracts
- Keep copies of contracts in a documented form
- Include review of third parties in your audit
- Utilize your ability to inspect if you have a clause that allows for it
In the infographic below, Jonathan identifies key considerations for ensuring the safety of your data. He highlights the need to take the proper steps to know who has your data. This includes verifying the legal review of vendor contracts that hold data and maintaining copies of vendor security assessments.
Shay Colson, one of our experts, wrote an excellent article on the inherent challenges of managing third-party cyber risk and how to adjust expectations to better fit business needs and strategically manage our resources to address the most pressing risks. It’s a must-read.
Your organization’s data security is increasingly dependent upon third parties, pressing the need for external reviews. Starting with a review of vendor contracts, focused on the key aspects that Jonathan and James shared in the video, helps set the course towards cyber resilience.






