Given the volume, depth of detail and uniqueness of the data they hold, law firms have emerged as prime targets for criminal networks. This comes as no surprise to most legal professionals and law firms who recognize the threat and have taken various steps to strengthen their defenses.
For example, the Legal Week Cyber Report 2018 found that more general counsel are taking a larger management role around cyber security issues: 45% said their role has expanded in the area of planning, 40% monitoring, 37% reporting and 43% responding to a cyber incident. From another perspective, a survey of 200 U.S. law firms last October revealed that 41% were planning to increase spending on cyber security tools and services in the next 12 months.
Yet, despite greater attention and increased spending, significant data breaches at law firms of all sizes continue to make news. From our investigative experience and what we know from global law enforcement agencies, law firms are being targeted by mainly a few tiers of cyber criminals. They range from ultra-sophisticated, well-backed criminal enterprises after specific high-value data to thieves looking for the easy win at firms with lax security.
Equally troubling, breached law firm data is showing up on the dark web alongside data that was not stolen, but rather accidentally exposed by employees or third parties. In May 2018, Kroll performed an analysis of the deep and dark web, and for every law firm in our sample, we found company emails and passwords up for grabs, creating a clear risk for fraudulent credential reuse. The source in many cases: employees who used their company email addresses to sign up for third party services.
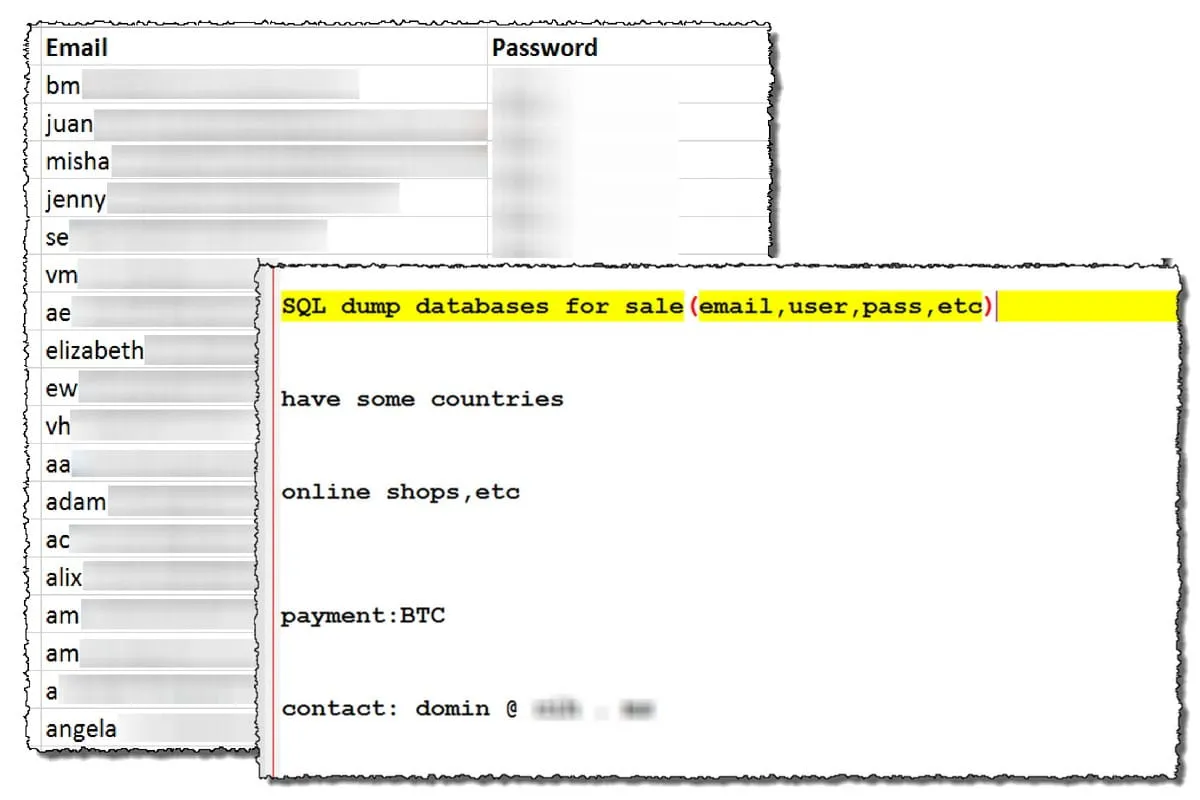
1- sample list of business email credentials and post on dark web forum selling access to larger database
With the trust of clients at stake, law firms are at a cyber security crossroads
At the heart of every attorney-client relationship is the client’s expectation that all forms of communications will be privileged and kept in strict confidence. In fact, the protections afforded by attorney-client privilege are why many clients primarily seek help from attorneys instead of potentially other professional advisors. The thought of client information breached, sold or otherwise divulged is the stuff of lawyers’ (and their clients’) nightmares.
Because current cyber security strategies are often coming up short, law firms should consider a more holistic approach, one that addresses data security from multiple directions but in an integrated way. Defensive measures continue to be a vital part of the security equation, but today, best practice also calls for sophisticated threat hunting, detection, investigation and response capabilities. This is the path to cyber resiliency, which enables you to more quickly and effectively neutralize harm caused by cyber criminals.
Cyber resiliency starts with a better understanding of the fundamentals: What do hackers want and why? How are they getting past existing defenses?
Law firm data can be monetized in a multitude of ways
Cyber criminals are among the most inventive and motivated people on the planet when it comes to monetizing data. The data held by law firms is particularly valuable because it can be leveraged in a multitude of ways – e.g., facilitating insider trading, setting up sophisticated counterfeiting operations, getting to government patent/trade offices or to market first by stealing intellectual property, running blackmail schemes or exercising personal vendettas that ruin reputations. Of course, there is always the irresistible appeal of stealing the identities of wealthy or well-connected clients for financial or other personal gain.
Primary tactics used by cyber criminals
Data losses at law firms can often be traced to one of three primary attack vectors:
- Phishing/Spearfishing/Business Email Compromise. This is currently the most common method of attack and research shows an average 27% success rate for phishing campaigns, with highly targeted ones reaching as high as 90%.
- Three main delivery methods account for the majority of ransomware infections: a user visits a compromised website that hides malicious code; a user opens a malicious email attachment; or a user clicks on a malicious link within an email message.
- Distributed Denial-of-Service (DDoS) Attacks. By overloading a firm’s servers, criminals severely disrupt the firm’s ability to conduct business. However, DDOS attacks may also serve as a distraction to conduct a more sophisticated attack.
People, processes, technology: three pillars of cyber resiliency
In our experience, organizations are best positioned to mitigate data-related threats if they take a multidimensional approach to cyber security. Whether you are a GC involved in managing cyber risk for your firm or a law firm of any size or clientele, the same principles apply: Integrate strategies that address people, processes and technology and you will be in a stronger position to protect your data, ultimately safeguarding your reputation and vital client relationships.
Information security is everyone’s responsibility
The vast majority of cyber-related vulnerabilities can be traced to staff and third parties who accidentally or deliberately don’t follow security protocols or are tricked into downloading malicious code.
Executive leadership and managing partners must set the tone at the top that information security is everyone’s responsibility.
Make employees and third parties your first line of defense by delivering ongoing security awareness campaigns and training, and then testing that training. Periodically remind users of basic best practices that include using company email accounts strictly for internal and client communications and carefully examining all incoming emails before clicking on any link or attachment. Also, employees should know how to raise an alert if they accidentally click on or open something suspicious.
Many organizations, including law firms, are finding great value in having a Chief Information Security Officer (CISO) on their executive team. This expert has the specialized technical knowledge and corporate governance experience to help organizations develop risk-based strategies appropriate for their needs. Engaging a virtual CISO on an interim or longer-term basis can be a good option for smaller firms or those in the midst of conducting an executive search.
Policies and processes set expectations
Several resources exist to help law firms create and implement policies and processes that promote information security, such as best practices outlined in SOC 2, ISO 27001, the NIST Cybersecurity Framework or CIS Controls.
At a minimum, law firms should have policies that address acceptable uses of corporate IT resources, data classification and “principle of least privilege”, mobile resources and social media, to name a few. Staff as well as third parties should be required to comply with all policies.
Additionally, law firms should strongly consider using restricted client portals that encrypt documents and messages to promote greater security. According to the American Bar Association TechReport 2017, many law firms aren’t using encryption for emails to clients, leaving the door open for hijacked communications, spoofed emails, etc.
Technology trends shifting to detection and containment
Given enough time and resources, a cyber criminal will eventually find a way into your law firm’s systems. Therefore, a more effective technology trend has been to deploy endpoint threat monitoring solutions, the most sophisticated of which reduce the burden of dealing with false positives and enable quick containment and remediation efforts.
Investing in a dark web monitoring solution can also alert you of potential threats that can originate from outside your network. For example, Kroll recently found several highly sensitive and attorney-client privileged documents belonging to one of our clients, a Fortune 100 global financial services company, exposed on the dark web. The source: a paralegal for one of our client’s outside law firms who was inadvertently disclosing this content while accessing free music and movies on P2P networks.
Clients need to know that their attorneys are protecting the sensitive information entrusted to them, and law firms need to take steps that signal their commitment to modern data security. By adopting more effective cyber security measures, law firms can help keep criminals at bay, preserve the trust of clients and stand out as a provider of choice in today’s highly competitive legal and professional services market.
"This article was originally published by LegalTech News."

