Key Takeaways
- Kroll identified a rise in phishing attacks targeting victims with a QR code to gain access to their network credentials.
- This tactic is particularly difficult to mitigate due to the nature of the QR code itself and protecting mobile devices.
- Ensuring businesses have updated proficient cybersecurity training for their employees, phishing-resistant MFA, and hardening guidelines are key recommendations to defend against this threat.
Kroll forensic examiners and threat intelligence analysts identified a new phishing tactic targeting individuals using QR codes. Victims receive phishing emails impersonating Microsoft, letting them know that additional security measures are required and asking victims to scan the QR code in the body of the email or the email attachment.
How QR Code Phishing Attacks Work
Once scanned, the user is led to a spoofed Microsoft log-in page where they are prompted to enter their credentials and password. Once the user enters their details on the malicious site, the attacker can access their accounts and the session token. Session token hijacking – where a hacker steals the session token to gain access to information, services or accounts – allows the attacker to pass as a legitimate user within the network or cloud environment.
As many users will already have multifactor authentication (MFA) in place, threat actors have needed to design updated techniques in order to convince a user to provide their username, their password, and their MFA through their “phish kit” unknowingly allowing for the interception of the session token response from the legitimate service, such as Microsoft Office 365. This tactic is commonly known as adversary in the middle (AitM) , where the attacker puts themselves within the authentication process to verify that a malicious user is the legitimate user.
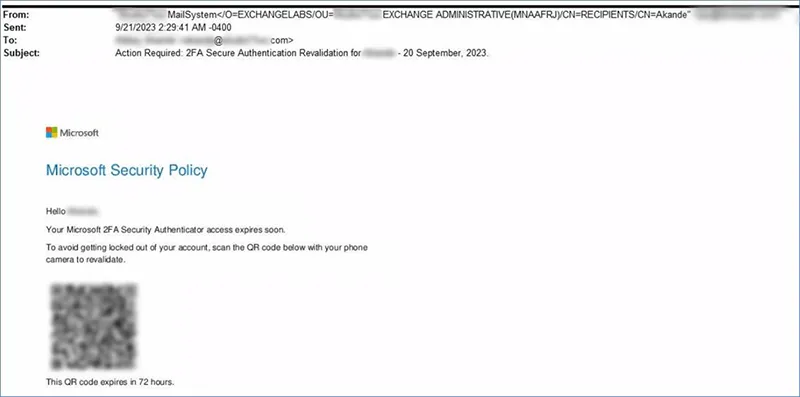
Figure 1: Example of phishing email asking for 2FA validation
The Motive
Most business email compromise (BEC) attacks, such as this one, are financially motivated. This means that once they have gained access, the attacker is not normally looking to exfiltrate data for extortion, like ransomware threat actors would be, but rather they are looking for opportunities to impersonate the victim to facilitate wire fraud, payroll deposits or invoice payment redirection. The threat actor will likely “sit” in the email account and perform recon for a few days, sometimes weeks, biding their time for an opportunity to jump into an email chain and take over the conversation in order redirect funds.
In some cases, the attacker might realize that the account they have infiltrated does not conduct the necessary processes for wire fraud or does not have the necessary permissions for the attacker to accomplish their means. It is then likely that they will send another phishing lure from the compromised email account to island hop to the victim they need.
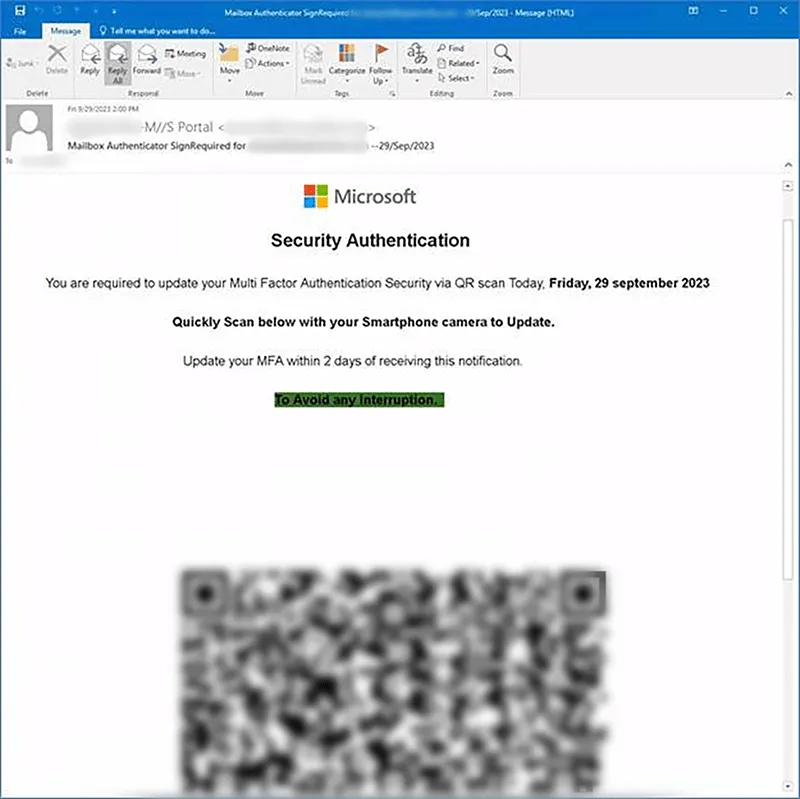
Figure 2: Example of phishing email asking for MFA update with a stringent timeline
Why QR Code Phishing Represents a Challenge:
Mobile devices are a weak link. In this attack, the user must use their mobile device to access the link, and typically, businesses – especially smaller ones – do not have a mobile device management (MDM) tool deployed on their employees’ work phones. This means that when the employee engages with the QR code using their mobile device, which is outside the business’s network controls, they are also outside the company’s security monitoring. This attack provides a way for an attacker to gain access to secured environment, such as email, using what is essentially an unguarded side entrance.
The nature of the QR code. Corporate cybersecurity training has drilled into users to keep an eye on suspicious-looking links. People know to look out for strange domain names or long URLs and not to click on these links. However, at first glance, a user cannot tell whether a QR code is malicious because they cannot identify the link behind the code visually or by hovering over it like one can with a traditional embedded link in an email. In other words, no immediately visible signs are in the QR code itself that would signal a user that the link is malicious. Further, if cybersecurity training does not mention that some phishing attempts might come in the format of a QR code, an employee might not make the connection that the technique being employed should be questioned and reported.
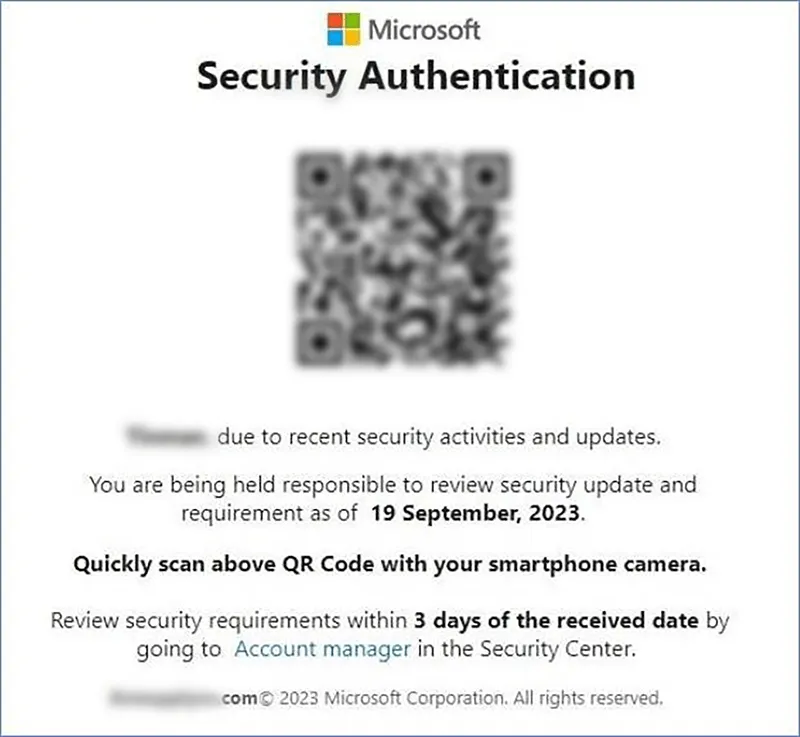
Figure 3: Example of phishing email asking for a security update with a stringent deadline
How to Detect or Prevent QR Code Phishing
Even though QR code phishing attacks can be tricky to avoid, a combination of stronger MDM controls, Phishing-resistant MFA, and updated cybersecurity training can be very effective. Here are a few ways in which businesses can be more prepared:
- MDM. As the name suggests, MDM software secures and enforces managed security policies on mobile devices. An MDM platform could provide security teams with the peace of mind that corporate network-connected devices remain secure. However, MDM software can be expensive, and many small and medium sized businesses typically do not have the budget to pay separately for an MDM tool. Despite this, it is one of the surest ways to mitigate attacks on mobile devices.
- Phishing resistant MFA. Of course, MFA is a recommended first line of attack as it solves some common attack methods such as password guessing. However, it does not solve all forms of credential theft as demonstrated in the example above. Phishing-resistant MFA – such as a smartcard or a physical security key – is designed to prevent MFA bypass attack scenarios as the valid user should be the only person with the physical key to login to their network.
- Cybersecurity training is vital. Remembering the fundamentals of cybersecurity training is still one of the best lines of defense. While the tactic is novel, there are still classic markers that demonstrate this is a phishing attempt despite the distracting QR code. In all the examples, there is a sense of urgency for the victim to scan within the next few hours or days. A strict deadline out of the blue is not something that a legitimate business or IT team would impose. Further, the emails stating the QR code will expire soon and including the sense of urgency to “scan now” are additional giveaways.
However, attackers are getting smarter, and Kroll has seen evidence of attackers spoofing internal IT support teams to try to trick employees further. However, if businesses continue to train their employees on an ongoing basis and update their training with the latest tactics, then employees should be able to recognize some of these telltale signs.
- Identity hardening guidelines. Businesses can use creative conditional access control (CAC) policies to reduce their attack surface. For example, if a corporate device policy only includes Windows for desktop and iOS mobile devices, block Android and MacBooks from authenticating. Additionally, organizations can disable or limit the scope of allowed MFA methods – such as SMS and voice approval or unused MFA application types – limit the number of allowed MFA devices per user and require extra authentication factors when authorizing MFA devices.
- Token protection. Microsoft also offers token protection, which attempts to reduce attacks using token theft, such as the one mentioned above, by ensuring a token is usable only from the intended device. Businesses can also reduce the duration of tokens so they expire sooner than the 90-day default setting. This won’t necessarily prevent an AitM attack, but it is a worthwhile additional layer of defense.
For Kroll Customers
Kroll's customers can request our Identity Hardening Tips from their account manager. If you have any other questions, please contact your technical account manager or submit a support ticket.
If you're unsure how to defend your organization against QR and other types of phishing attempts, get in touch with a Kroll expert today.

