Key Takeaways
- Kroll has observed DARKGATE malware being delivered to users through files shared in Microsoft Teams messages.
- These campaigns have targeted the transportation and hospitality sectors.
- Files hosted to public SharePoint sites were downloaded and executed by victims, which led to batch scripts copying the AutoIT interpreter and scripts from adversary-controlled infrastructure.
- The DARKGATE payload was injected into a running process and further AutoIt scripts were created and used for persistence in the user’s Start Menu.
- This appears to be part of a wider DARKGATE campaign, also reported across open-source.
- This continues a surge of Microsoft Teams-related social engineering observed since Q2 2023, following the identification of a vulnerability in Teams that relies on organizational configuration changes and user awareness to mitigate.
Summary
Kroll has observed an uptick in cases of DARKGATE malware being delivered through Microsoft Teams messages. These campaigns have mainly targeted organizations in the transportation and hospitality sectors. This activity has also been reported throughout open-source reporting, sharing a number of key indicators with Kroll observations, such as common filenames, adversary infrastructure and similar domain name conventions to host the initial download.
Kroll observed that the file was hosted on a public SharePoint site and was initially delivered to several victims via Microsoft Teams messages. The file that was hosted on this site and downloaded by the victim was "C_onfidential Sign_ificant Company Changes[.]zip", which appears to be part of a generic list of lure filenames for this campaign. Other examples of filenames observed both by Kroll and open-source reporting include “Vacation schedule[.]zip”, “Reduction of employees[.]zip” and “Repair[.]zip”. Both the filenames themselves—and the fact that they have been observed across multiple cases—leads us to assess that the lures are almost certainly part of a generic preset list of lures, rather than targeted social engineering specifically towards the victim organization.

Figure 1 – DARKGATE Attack Chain
DARKGATE Attack Chain
The downloaded zip file contained a .LNK file named identical to the zip file. Once executed, the .LNK file runs a batch script, which writes out and executes a Visual Basic script. This script first creates a directory, then copies curl.exe into the directory using a random filename. Next, it uses the renamed curl executable to download the legitimate AutoIt script interpreter and a malicious AutoIt script from the IP: 5[.]188[.]87[.]58. This script injected a payload into legitimate processes already in memory, which was identified as DARKGATE. After the code was injected, the target process would create an AutoIT script that was unique to each host. It also created a shortcut in the user’s Start Menu to automatically launch the script on each login. This allows for persistence across user sessions.
What is DARKGATE?
DARKGATE is a Windows-based malware that has capabilities ranging from cryptocurrency mining, file encryption, credential stealing and remote access to victim endpoints. It was first publicly reported in 2018; however, the author made a post in May 2023 stating they have decided to rent out the malware for a daily ($333), monthly ($10,000) or lifetime ($100,000) subscription fee. In the post, they list the extensive suggested features of the malware, which identifies its full suite of capabilities, from keylogging and privilege escalation to bot and file management. A full list of these can be found in Figure 2.
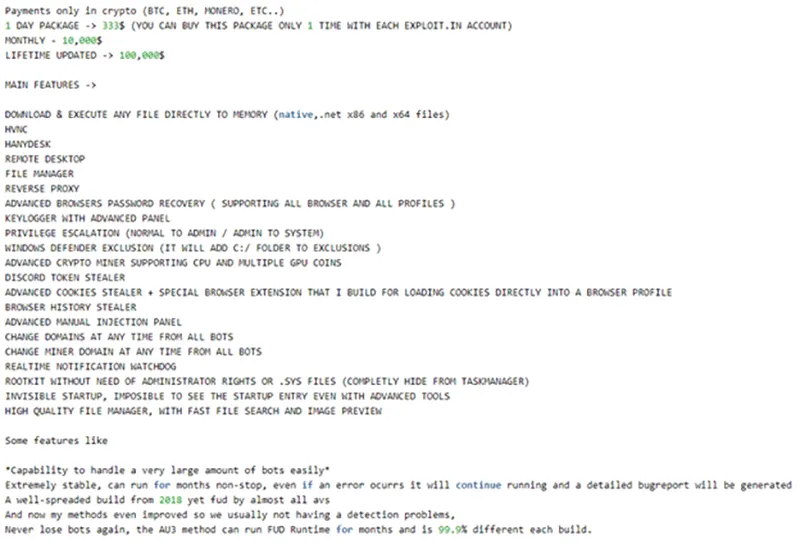
Figure 2 - DARKGATE Author Post Extract
Microsoft Teams Used for Initial Access
Although it is not fully understood how the threat actor in this campaign delivered the initial Teams messages to victims, there has been reporting on how initial access could be achieved using Teams since Q2 2023. This led to the tool “TeamsPhisher” being released on Github, which operationalizes sending attachments to victims on Teams on a larger scale. The tool combines ideas from JUMPSEC's researchers, techniques from Andrea Santese and authentication functions from Bastian Kanbach's “TeamsEnum” tool. The tool verifies target users' ability to receive external messages, then creates a new thread and sends the victim a message with a SharePoint attachment link. TeamsPhisher requires a Microsoft Business account with valid Teams and SharePoint licenses, and it offers features like preview mode, secure file links, delay specification and logging. It is therefore likely that the threat actor behind the ongoing DARKGATE campaign is utilizing a similar tool to TeamsPhisher to facilitate initial access.
There has also been reporting by Microsoft stating that a threat actor, tracked by Microsoft as “Storm-0324,” has begun to use Teams-based phishing as their initial access vector, shifting from traditional email phishing. They have been observed using the TeamsPhisher tool to deliver phishing attachments to victims, which ultimately led to JSSLOADER and additional post-compromise tooling. Furthermore, in August 2023, Microsoft reported that “Midnight Blizzard,” also known as APT29, expanded their social engineering techniques by sending victims a Teams message request masquerading as technical support or the organization’s security team (Figure 3). If accepted, this could lead to attempts to steal multi-factor authentication (MFA) tokens from the victim, and grant access to the account (assuming previous credentials were accessed by the actor).
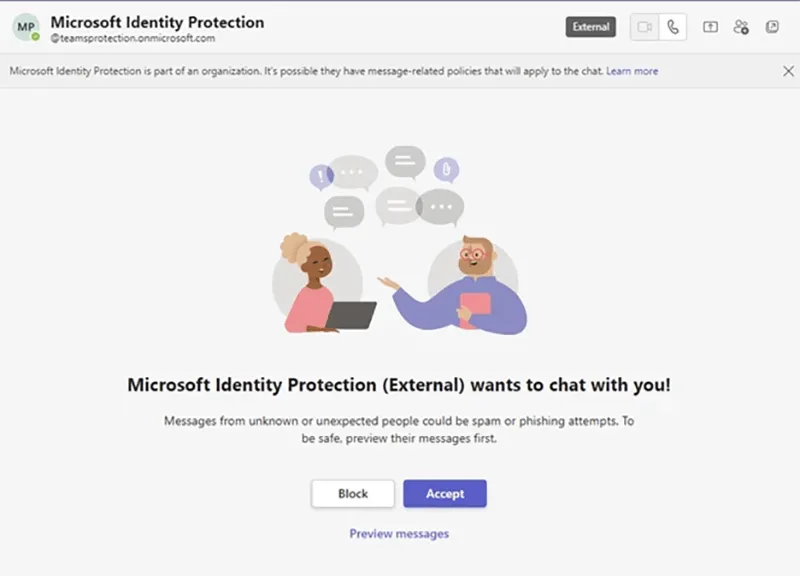
Figure 3 - Midnight Blizzard (APT29) Teams Social Engineering
Teams-related phishing has seen a surge in recent months, with the DARKGATE campaign being the latest in successful social engineering that Kroll has observed. But, this is not just limited to DARKGATE; rather, the emergence of publicly available tooling has made this vector widely accessible to any threat actor that currently uses, or plans to use, social engineering as an initial access vector against an organization.
Key Recommendations
- For organizations that use Microsoft Teams, it is recommended to assess the business requirement for external tenants to have permissions to message inbound to your organization on Teams. This access can be removed entirely from the Microsoft Teams Admin Center.
- If external access is required, it is recommended to review the Teams security settings to only allow communication from domains on an allow-list.
- Provide security awareness training to employees on the potential risks of opening files or interacting with unknown senders through Microsoft Teams.





