The Kroll Artifact Parser and Extractor (KAPE) utilizes Targets and Modules to collect and parse digital evidence. Its Compound Targets and Compound Modules call upon other Targets and Modules in order to collect and parse the most important data as efficiently as possible. One of KAPE’s most widely used Compound Targets for incident response (IR) is KapeTriage.
In particular, the KapeTriage Compound Target was created to selectively collect the most important artifacts from a computer in minutes, rather than creating a full disk image, with forensically reliable, quick win results.
Numerous components exist within the KapeTriage Compound Target that have various relationships between data points. Our KapeTriage MindMap provides a hierarchical outline of the KapeTriage Compound Target and, at a glance, shows how various segments collectively deliver the most relevant results for efficient, yet nuanced, IR investigations. Our KapeTriage MindMap can be downloaded for personal use here.
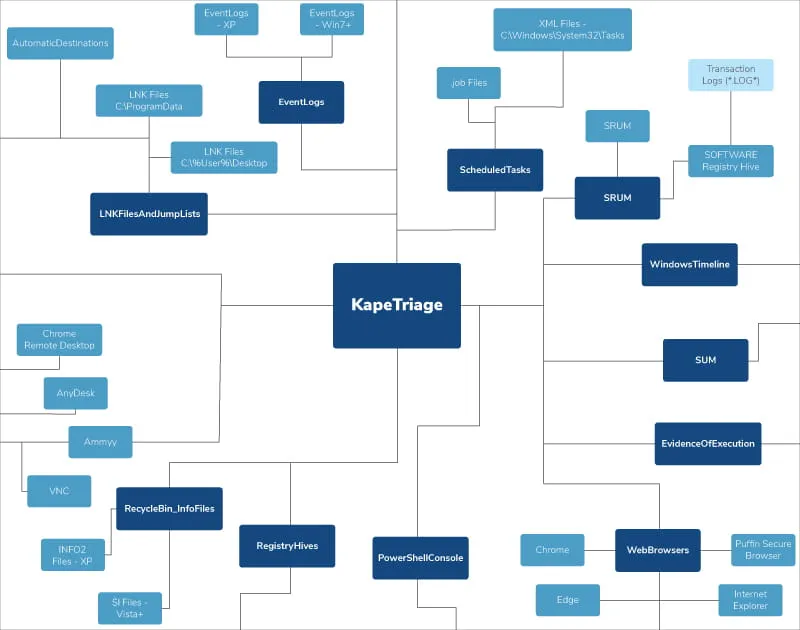
Foundational Segments Powering KapeTriage Compound Target
EventLogs
The EventLogs Target collects both the legacy Microsoft Windows Event Log format (.evt) featured in Windows XP/Server 2003 and prior versions as well as the current Windows Event Log format (.evtx) featured in Windows Vista to present-day versions of Windows and Windows Server.
LNKFilesAndJumpLists
The LNKFilesAndJumpLists Target collects .LNK files from their respective locations within various versions of Windows. .LNK files provide evidence indicative of file access.
FileSystem
The FileSystem Target collects various important NTFS metadata artifacts, most notably, the $MFT and $J artifacts. The $MFT will provide an examiner with insight into the file system contents of the partition from which the $MFT was collected. The $J will provide a historical look into what changes occurred to files that reside within the NTFS partition.
PowerShellConsole
The PowerShellConsole Target collects the ConsoleHost_history.txt file, which contains a history of PowerShell commands run by a given user. Please note that this file does not get parsed by a tool since it is simply a text file. Be sure to check for the presence of this file if it may possibly relate to your case.
RecycleBin_InfoFiles
The RecycleBin_InfoFiles Target collects metadata files that reside within a user’s Recycle Bin. Parsing these files will provide information about which files were deleted by a given user. These files do NOT contain the original files that were deleted. To collect the original files that were deleted, use the RecycleBin_DataFiles.tkape Target in addition to this one.
RegistryHives
The RegistryHives Target collects the Registry Hives specified within the following Targets: RegistryHivesSystem.tkape and RegistryHivesUser.tkape. This means the following Registry Hives will be collected: SAM, SOFTWARE, SYSTEM, SECURITY, NTUSER.dat, DEFAULT, UsrClass.dat.
RemoteAdmin
The RemoteAdmin Target collects files related to various Remote Administration Tools (RAT), including but not limited to AnyDesk, TeamViewer and ScreenConnect. Each RAT leaves behind a presence on the file system for which each respective KAPE Target has been curated.
ScheduledTasks
The ScheduledTasks Target collects files related to Scheduled Tasks. Please note that Scheduled Tasks activity may also reside in Event Logs.
SRUM
The SRUM Target collects the SOFTWARE Registry Hive and the SRUDB.dat file that contains the System Resource Usage Monitor (SRUM) database. The SRUM database can provide invaluable information about which processes within the last 30 days wrote to or read from disk and sent and received bytes.
SUM
The SUM Target collects .mdb files related to the SUM database, which can provide critical information about which users authenticated to which hosts within a given domain. Additionally, Domain Controllers may contain a DNSInfo database that can provide a domain’s DNS history going back as far as three years.
WindowsTimeline
The WindowsTimeline Target collects an SQLite database only found on Windows 10 that can provide evidence of execution for a given user. Please note that this artifact did not exist before Windows 10, and it was discontinued in Windows 11.
Antivirus
The Antivirus Target collects files related to various antivirus/Endpoint Detection and Response (EDR) software, including but not limited to Windows Defender, Symantec and SentinelOne. Each antivirus software leaves behind a presence on the file system in the form of either quarantine logs, detection logs and/or quarantined files. Please note that some antivirus software also logs entries to the Application Event Log. Look for the name of a given antivirus software as the Provider within the Application Event Log.
EvidenceOfExecution
The EvidenceOfExecution Target will collect files related to various program execution artifacts, including Prefetch and Amcache that reside within Windows.
WebBrowsers
The WebBrowsers Target will collect files related to various popular web browsers. Please note that most Chromium (SQLite) browser artifacts will have similar, if not identical, artifact filenames. Firefox (SQLite) and Internet Explorer/older versions of Edge (ESE) will be significantly different from any Chromium-based browser.
The KapeTriage MindMap can be a valuable resource when looking to understand the relationships between components and how the components work together. It can be downloaded for personal use here.
The KapeTriage Compound Target is constantly being refined as we and the DFIR community discover new artifacts that may assist an IR investigation so keep KAPE updated for the latest advancements to Targets and Modules. If you are interested in learning more about KAPE or becoming KAPE certified, explore our virtual live training and certification opportunities or contact our experts at [email protected]. An enterprise license is required when KAPE is used on a third-party network and/or as part of a paid engagement.


