With the holiday season upon us, retailers and shoppers alike should be extra vigilant for suspicious emails and links attempting to leave behind a gift that nobody wants – ransomware. Ransomware attacks across industry sectors are reported to be up some 500% from this time last year, and retailers appear to be especially hard-hit. A review of Kroll’s 2019 client intake statistics shows that one in three cyber incidents reported by retailers involved malware, including point-of-sale compromise, banking Trojans, and ransomware (Figure 1).
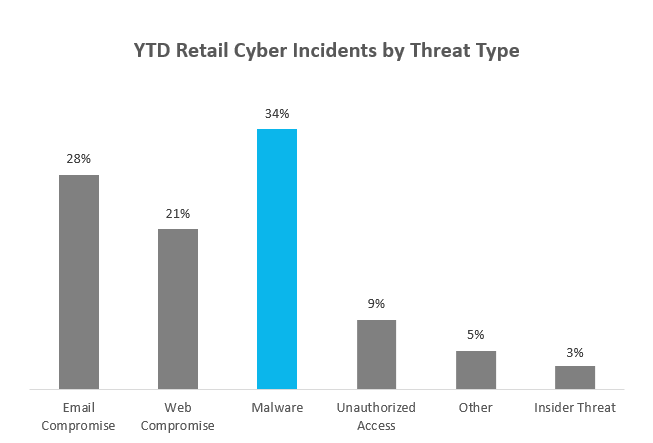
Figure 1: Percentage of Retail Client Cyber Incidents by Threat Type
Cyberattacks historically spike between the start of Thanksgiving and Black Friday and end of Christmas. In 2018, researchers looking at the nine-day shopping window around Thanksgiving, which includes Black Friday, Small Business Saturday and Cyber Monday, noted a 432% increase in ransomware attacks over the similar time period in 2017. All three of these shopping days are characterized by an increase in user clicks on emails, websites, advertising pop-ups and other vectors commonly associated with cyberattacks.
“Threat actor groups, seeing the profits made this summer by targeting organizations like schools with ransomware, may be looking carefully now at the retail sector; they know that keeping systems on-line for sales will be a number one priority for retailers this season,” says Kroll Associate Managing Director Keith Wojcieszek. “A significant ransomware attack on a retailer could result in the crash of an ecommerce platform or the inability for cashiers to process transactions. Retailers experiencing such a hit may be more likely to pay a hefty ransom to avoid an impact on holiday profits.
Beware Email Messages Bearing Discounts and Special Sales
The Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3) recently noted that one of the most common vectors for ransomware attack is an email phishing campaign. This time of year, threat actors prey on the fact that individuals, including retail employees, will be looking for email messages offering sales and discounts or tracking shipments. A spoofed email message appearing to be from a familiar and trusted company can inject malware when users click malicious files or links.
Kroll incident responders report that such links or attachments act as the first step of a two-part attack. Step one occurs when users click on bad links and their machine is infected with a banking Trojan such as Emotet or TrickBot meant to harvest log-in credentials. Step two happens when Ryuk ransomware is deployed as a secondary dropper to the Trojan, encrypting network files and folders and demanding a ransom.
How to Beat the Holiday Ransomware Blues
According to Managing Director Steve Kopeck, retailers can work to prevent ransomware incidents by enhancing both human and technical defenses. “While employee security awareness is vital throughout the year, retailers might want to consider pushing out refresher training or specific holiday-related ‘pop-up’ alerts. A timely reminder to employees to use caution when viewing or opening emails and email attachments can make all the difference in averting a complete system lockup,” says Steve.
Steve notes that retailers should likewise revisit or enhance technical strategies that should already be in place given they are best practices to follow throughout the year. “Advanced technology solutions exist that recognize phishing emails and thus help keep malicious messages from entering corporate inboxes,” explains Steve. “Another expedient measure is to configure the email system to flag emails that originate from external parties; something as simple as the word ‘external’ in the subject line will alert the recipient that while the sender might look to be someone internal, in reality they are dealing with an external party.”
Steve also advises that organizations should take time to specifically review their email configurations to harden the overall environment. “Threat actor will often move on to an easier target if they encounter obstacles too time-consuming to overcome. Unfortunately, we have observed clients experience worst-case scenarios that could have been prevented had stringent controls been defending their environment,” says Steve. Some of the best practices he recommends to retailers include the following: employ a configuration for internet-facing servers that disables or blocks unnecessary services, ports and/or accounts; does not use default ports; changes or updates default log-in credentials; and restricts access to administrative functions, APIs and/or panels.
Ultimately, locking down remote access is imperative, declares Managing Director J. Andrew Valentine, with a particular reminder about Remote Desktop Protocol (RDP). “Ensure that RDP is not open to the internet via single-factor authentication anywhere in the organization,” says Andrew. “Brick and mortar retailers should pay special attention that PowerShell in the cardholder data environment is disabled.” While PowerShell is a legitimate Microsoft Windows script, cybercriminals will leverage it to hide malicious code and avoid ready detection.
Did Your Holiday Planning Include Proactive Cyber Preparations?
As a retailer, you have been planning for months for the holiday season. If your plans didn’t include a review of your cyber defenses, don’t let all your hard work go to waste now. You still have time to implement cyber security measures that can help you deter malware attacks and focus instead on working to ring up your best sales ever.


